When Ransomware Gangs Get Careless
Cyber Fail
,
Fraud Management & Cybercrime
,
Ransomware
Also: Rampant App Vulnerabilities, Cloud Misconfiguration and Why CISOs Matter
Welcome to “Cyber Fail,” where our experts uncover fails so we can all strengthen our defenses. Today, we examine what happens when ransomware groups get careless, application developers’ laissez-faire attitude toward vulnerabilities, and the security woes of a beleaguered crypto exchange.
See Also: OnDemand Panel | Securing Operational Excellence: Thwarting CISOs 5 Top Security Concerns
In this episode:
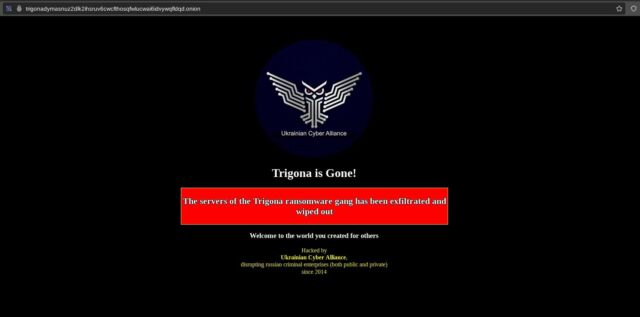
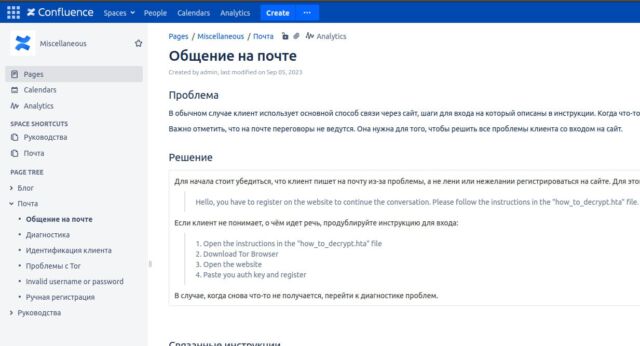
- When Ransomware Gangs Get Careless. Security researcher Brian Krebs recently poked around the 8Base ransomware group’s data leak site and found an error page that yielded a wealth of information about the developer who built it. Here’s what happens when cybercriminals are negligent.
- Hacking the Human Brain. News that the U.S. Food and Drug Administration approved a request from Elon Musk startup Neuralink for human testing of a neural link to the brain deserves a moment of introspection.
- Passwords? Who Needs Passwords? Investigators finally got to the bottom of how bad actors hacked into the DC Health Link insurance system and compromised the personal information of 56,000 Washington, D.C., residents – including members of Congress. Was it a convincing phishing email? Highly sophisticated malware? Of course not!
- App Security: What, Me…