US indicts heart doctor for allegedly spearheading high-profile ransomware operations
A 55-year-old Venezuelan cardiologist has been charged in the US over allegedly being the mastermind behind the Jigsaw and Thanos ransomware operations.
Charges against Moises Luis Zagala Gonzalez were unsealed in federal court in Brooklyn, New York, on Monday and concern his alleged use and sale of ransomware, in addition to his support of and profit-sharing with other cyber criminals.
Zagala resides in Ciudad Bolivar, Venezuela and also has citizenship in France. He is alleged to have created multiple high-profile ransomware tools in his spare time while primarily being a practising doctor.
A Federal Bureau of Investigation (FBI) source posed as a prospective cyber criminal and was able to discover how Zagala’s operation ran, how he generated multiple revenue streams, and how he ‘coached’ the cyber criminals into being more successful using the tools he created.
Zagala is alleged to have created the Jigsaw ransomware strain as well as the Thanos ‘ransomware builder’ – an application that allowed users to build their own ransomware program to be used alone or sold to the wider community.
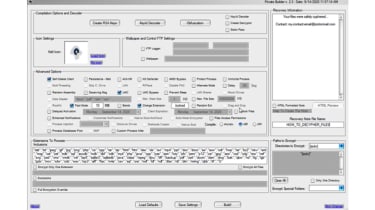
The Thanos application presented users with a GUI and an assortment of checkboxes to enable and disable certain features so effective ransomware programs could be built with little technical knowledge.
Such features included a data stealer that allowed users to select which types of files were stolen from a victim, an anti-VM feature that prevented researchers from loading it into a virtual machine for analysis and a self-delete function that destroyed the program after its use had become exhausted.
Through the FBI’s source, the Bureau was able to understand how Thanos was sold through two licensing models.
Prospective users could either pay a single up-front fee for a limited license and have access to the program for a set time, or enrol into an affiliate program which saw the user receive a lifetime license in return for giving Zagala a portion of the profit generated from the ransomware it created.
The Depart of Justice (DoJ) said Zagala owned a server in Charlotte, North Carolina that checked if a user’s license was valid or not.
After the FBI source request to join Zagala’s affiliate…