Ransomware Dwell Time Hits Low Of 24 Hours
(MENAFN– PR Newswire)
Analysis from Secureworks annual State of The Threat Report shows ransomware median dwell time has dropped from 4.5 days to less than 24 hours in a year
ATLANTA, Oct. 5, 2023 /PRNewswire/ — Ransomware is being deployed within one day of initial access in more than 50% of engagements, says Secureworks® (NASDAQ: SCWX ) Counter Threat UnitTM (CTUTM). In just 12 months the median dwell time identified in the annual Secureworks State of the Threat Report has freefallen from 4.5 days to less than one day. In 10% of cases, ransomware was even deployed within five hours of initial access.
“The driver for the reduction in median dwell time is likely due to the cybercriminals’ desire for a lower chance of detection. The cybersecurity industry has become much more adept at detecting activity that is a precursor to ransomware. As a result, threat actors are focusing on simpler and quicker to implement operations, rather than big, multi-site enterprise-wide encryption events that are significantly more complex. But the risk from those attacks is still high,” said Don Smith, VP Threat Intelligence, Secureworks Counter Threat Unit.
“While we still see familiar names as the most active threat actors, the emergence of several new and very active threat groups is fuelling a significant rise in victim and data leaks. Despite high profile takedowns and sanctions, cybercriminals are masters of adaptation, and so the threat continues to gather pace,” Smith continued.
The annual State of the Threat report examines the cybersecurity landscape from June 2022 to July 2023. Key findings include:
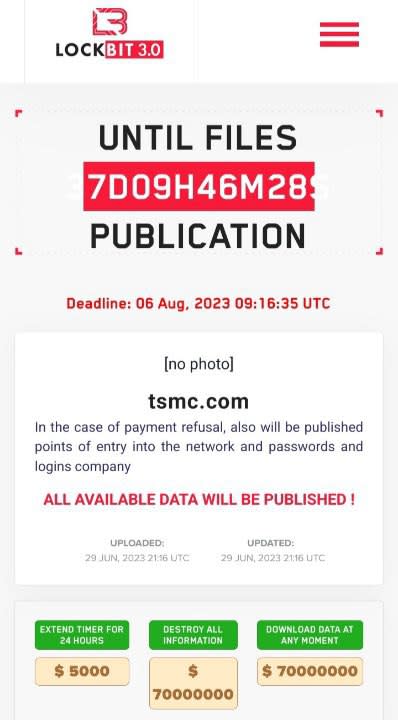
While some familiar names including GOLD MYSTIC (LockBit), GOLD BLAZER (BlackCat/ALPV), and GOLD TAHOE (Cl0p) still dominate the ransomware landscape, new groups are emerging and listing significant victim counts on ” name and shame” leak sites . The past four months of this reporting period have been the most prolific for victim numbers since name-and-shame attacks started in 2019.
The three largest initial access vectors (IAV) observed in ransomware engagements where customers engaged Secureworks incident responders were: scan-and-exploit,…