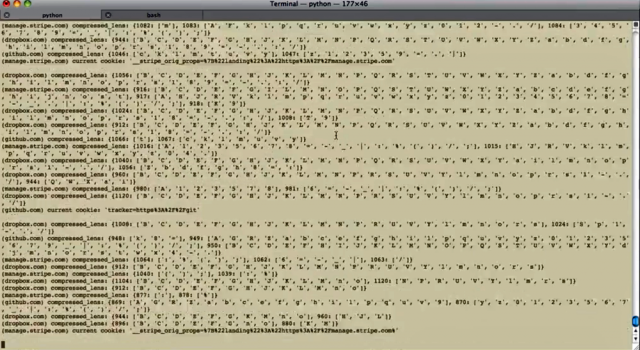
A screen shot from a video showing CRIME decrypting the contents of an encrypted cookie used to authenticate a dropbox.com user account.
Researchers have identified a security weakness that allows them to hijack web browser sessions even when they’re protected by the HTTPS encryption that banks and e-commerce sites use to prevent snooping on sensitive transactions.
The technique exploits web sessions protected by the Secure Sockets Layer and Transport Layer Security protocols when they use one of two data-compression schemes designed to reduce network congestion or the time it takes for webpages to load. Short for Compression Ratio Info-leak Made Easy, CRIME works only when both the browser and server support TLS compression or SPDY, an open networking protocol used by both Google and Twitter. Microsoft’s Internet Explorer, Google’s Chrome and Mozilla’s Firefox browsers are all believed to be immune to the attack, but at time of writing smartphone browsers and a myriad of other applications that rely on TLS are believed to remain vulnerable.
CRIME is the latest black eye for the widely used encryption protocols, which act as the Internet’s foundation of trust by encrypting traffic that flows over open networks and cryptographically proving websites such as Gmail are really operated by Google rather than criminal hackers or state-sponsored spies. The specter of a new attack that could subvert one of the only widely available protections preventing the interception of sensitive e-mails and web transactions, follows revelations that both Iran and China have actively worked to defeat it so they could spy on its citizens.
Read 16 remaining paragraphs | Comments

Ars Technica » Technology Lab
![]()
![]()
