HTTPS for everyone: WordPress adds encryption for all customer sites
Serving up your website using HTTPS is good for security and for search engine reputation, so WordPress will do it for you, just like that.
Naked Security – Sophos
Serving up your website using HTTPS is good for security and for search engine reputation, so WordPress will do it for you, just like that.
Naked Security – Sophos
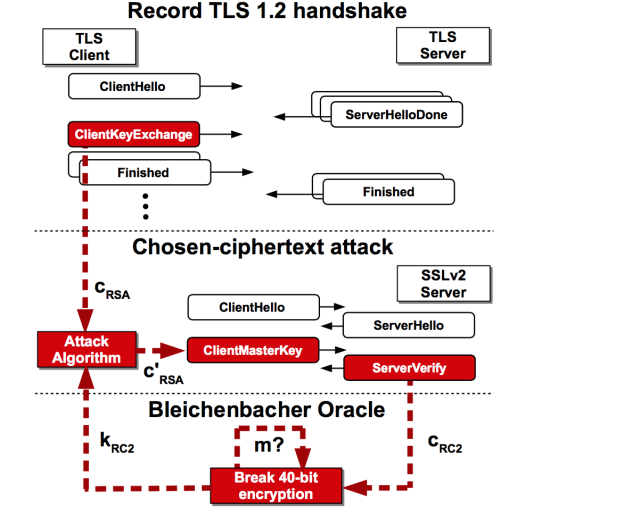
Enlarge (credit: Aviram et al.)
More than 11 million websites and e-mail services protected by the transport layer security protocol are vulnerable to a newly discovered, low-cost attack that decrypts sensitive communications in a matter of hours and in some cases almost immediately, an international team of researchers warned Tuesday. More than 81,000 of the top 1 million most popular Web properties are among the vulnerable HTTPS-protected sites.
The attack works against TLS-protected communications that rely on the RSA cryptosystem when the key is exposed even indirectly through SSLv2, a TLS precursor that was retired almost two decades ago because of crippling weaknesses. The vulnerability allows an attacker to decrypt an intercepted TLS connection by repeatedly using SSLv2 to make connections to a server. In the process, the attacker learns a few bits of information about the encryption key each time. While many security experts believed the removal of SSLv2 support from browser and e-mail clients prevented abuse of the legacy protocol, some misconfigured TLS implementations still tacitly support the legacy protocol when an end-user computer specifically requests its use. The most notable implementation subject to such fatal misconfigurations is the OpenSSL cryptographic library, which on Tuesday is expected to release an update that makes such settings much less likely to occur.
Recent scans of the Internet at large show that more than 5.9 million Web servers, comprising 17 percent of all HTTPS-protected machines, directly support SSLv2. The same scans reveal that at least 936,000 TLS-protected e-mail servers also support the insecure protocol. That’s a troubling finding, given widely repeated advice that SSLv2—short for secure sockets layer version 2—be disabled. More troubling still, even when a server doesn’t allow SSLv2 connections, it may still be susceptible to attack if the underlying RSA key pair is reused on a separate server that does support the old protocol. A website, for instance, that forbids SSLv2 may still be vulnerable if its key is used on an e-mail server that allows SSLv2. By the researchers’ estimate, that leaves 11.5 million HTTPS-protected websites and a significant number of TLS-protected e-mail servers open to attack.
If you thought MD5 was banished from HTTPS encryption, you’d be wrong. It turns out the fatally weak cryptographic hash function, along with its only slightly stronger SHA1 cousin, are still widely used in the transport layer security protocol that underpins HTTPS. Now, researchers have devised a series of attacks that exploit the weaknesses to break or degrade key protections provided not only by HTTPS but also other encryption protocols, including Internet Protocol Security and secure shell.
The attacks have been dubbed SLOTH—short for security losses from obsolete and truncated transcript hashes. The name is also a not-so-subtle rebuke of the collective laziness of the community that maintains crucial security regimens forming a cornerstone of Internet security. And if the criticism seems harsh, consider this: MD5-based signatures weren’t introduced in TLS until version 1.2, which was released in 2008. That was the same year researchers exploited cryptographic weaknesses in MD5 that allowed them to spoof valid HTTPS certificates for any domain they wanted. Although SHA1 is considerably more resistant to so-called cryptographic collision attacks, it too is considered to be at least theoretically broken. (MD5 signatures were subsequently banned in TLS certificates but not other key aspects of the protocol.)
“Notably, we have found a number of unsafe uses of MD5 in various Internet protocols, yielding exploitable chosen-prefix and generic collision attacks,” the researchers wrote in a technical paper scheduled to be discussed Wednesday at the Real World Cryptography Conference 2016 in Stanford, California. “We also found several unsafe uses of SHA1 that will become dangerous when more efficient collision-finding algorithms for SHA1 are discovered.”
Inherent insecurity in the routing protocol that links networks on the Internet poses a direct threat to the infrastructure that secures communications between users and websites.
The Border Gateway Protocol (BGP), which is used by computer network operators to exchange information about which Internet Protocol (IP) addresses they own and how they should be routed, was designed at a time when the Internet was small and operators trusted each other implicitly, without any form of validation.
If one operator, or autonomous system (AS), advertises routes for a block of IP addresses that it doesn’t own and its upstream provider passes on the information to others, the traffic intended for those addresses might get sent to the rogue operator.
To read this article in full or to leave a comment, please click here