ISG Executive Insights helps users manage their complex supplier ecosystems
Information Services Group (ISG) launched ISG Executive Insights, a market intelligence and data analytics platform that addresses the challenges of managing increasingly complex supplier ecosystems.
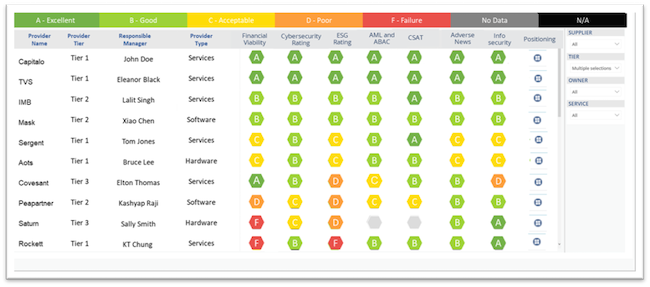
With ISG Executive Insights, organizations can now gather insights in one platform to optimize provider relationships, risk and compliance. The new data-analytics-as-a-solution offering is powered by ISG’s data repository, a comprehensive, curated database of global IT, business process and engineering outsourcing contracts—paired with ISG’s patented IT price benchmarking, market cost intelligence and other analytical tools.
Leveraging data from more than 180,000 sourcing contracts, 5,600 unique assessments and 1.3 million deliverables and obligations, ISG Executive Insights delivers market trends and forecasts; information on provider capabilities, pricing and commercial terms; real-time analytics, risk mitigation and ongoing, post-deal value realization.
Enterprise leaders can quickly access intelligence on which suppliers have created value for the business, how spending compares with the market, how provider projects are performing and what governance and operational best practices need to be adopted.
“No other technology research and advisory firm can offer the same level of actionable data and insights as ISG,” said Todd Lavieri, vice chairman and president, ISG Americas and Asia Pacific.
“To make the best decisions, enterprises increasingly need current and meaningful data from the market, their organizations, and their ecosystems of partners and relationships,” Lavieri said. “ISG Executive Insights turns the data we gather and analyze in the course of advising on more than $18 billion of annual contract value every year into actionable intelligence for global clients and all ecosystem participants across all sectors of the marketplace. There is no other platform like it.”
Enterprises can use the platform to manage performance and spending, mitigate risk and foster innovation with data-powered profiles of provider capabilities and risk, intuitive dashboards, price intelligence, mobile network maps, on-demand assessments, continuous monitoring,…


