SEC is investigating MOVEit mass-hack, says Progress Software
U.S. securities regulators have opened a probe into the MOVEit mass-hack that has exposed the personal data of at least 64 million people, according to the company that made the affected software.
In a regulatory filing this week, Progress Software confirmed it had received a subpoena from the U.S. Securities and Exchange Commission (SEC) seeking “various documents and information” relating to the MOVEit vulnerability. “The SEC investigation is a fact-finding inquiry, the investigation does not mean that Progress or anyone else has violated federal securities laws,” Progress said, adding that it intends to “cooperate fully” with the investigation.
Progress also said in the filing that it expects to see minimal financial impact from the MOVEit mass-hacks, despite the broad scale of the incident.
The company said it incurred $1 million of costs related to the MOVEit vulnerability, once it had taken into account received and expected insurance payouts of approximately $1.9 million.
However, Progress notes that a loss from this incident remains possible after 23 affected customers launched legal action against the company and “intend to seek indemnification.” Progress said that a further 58 class action lawsuits have been filed by individuals who claim to be affected.
While it’s almost six months on from the discovery of the MOVEit zero-day vulnerability, the exact number of impacted MOVEit Transfer customers remains unknown, though cybersecurity company Emsisoft reports that 2,546 organizations have so far confirmed to be affected, impacting more than 64 million individuals.
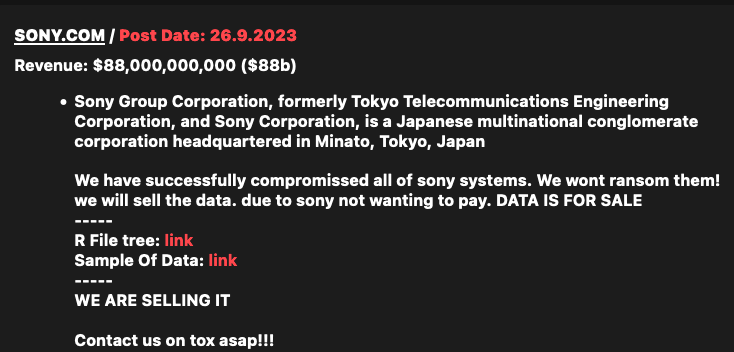
New victims continue to come forward. Last week, Sony confirmed that more than 6,000 employees had data accessed in a MOVEit-related incident, and Flagstar Bank said more than 800,000 customer records had been stolen.
November security incident
Progress Software said in the filing that it expects to incur additional costs of $4.2 million related to a separate cybersecurity incident in November 2022.
The filing doesn’t reveal any details about the incident, but John Eddy, a Progress spokesperson representing the company via a third-party agency, confirmed that Progress Software at the time uncovered…