Tag Archive for: investigation
Atomic Wallet Hack Exposes $35 Million Crypto Asset Theft – An In-depth Look at the Aftermath and Ongoing Investigation
/in Computer Security
Join Our Telegram channel to stay up to date on breaking news coverage
The Atomic Wallet hack has shaken the crypto community, causing substantial user losses and prompting an urgent investigation. Here’s a closer look at the aftermath, recovery efforts, and the wider landscape of cryptocurrency breaches, along with Atomic Wallet’s response to the incident.
Atomic Wallet Hack Reveals $35 Million in Crypto Asset Theft
An analysis conducted by on-chain investigator ZachXBT reveals that Atomic Wallet users have suffered crypto asset theft amounting to at least $35 million since June 2. Among these losses, the five largest account for $17 million.
After the attack, Atomic Wallet took to Twitter to inform users that they were actively conducting an investigation into the cause of the incident. Troubling accounts have surfaced, revealing instances of token losses, erasure of transaction histories, and even the outright theft of entire crypto portfolios.
ZachXBT, a pseudonymous Twitter user known for tracking stolen crypto funds and aiding hacked projects, independently conducted an investigation. According to ZachXBT’s findings, the largest victim lost $7.95 million in Tether (USDT). ZachXBT commented that the total amount stolen could potentially exceed $50 million as more victims continue to be discovered.
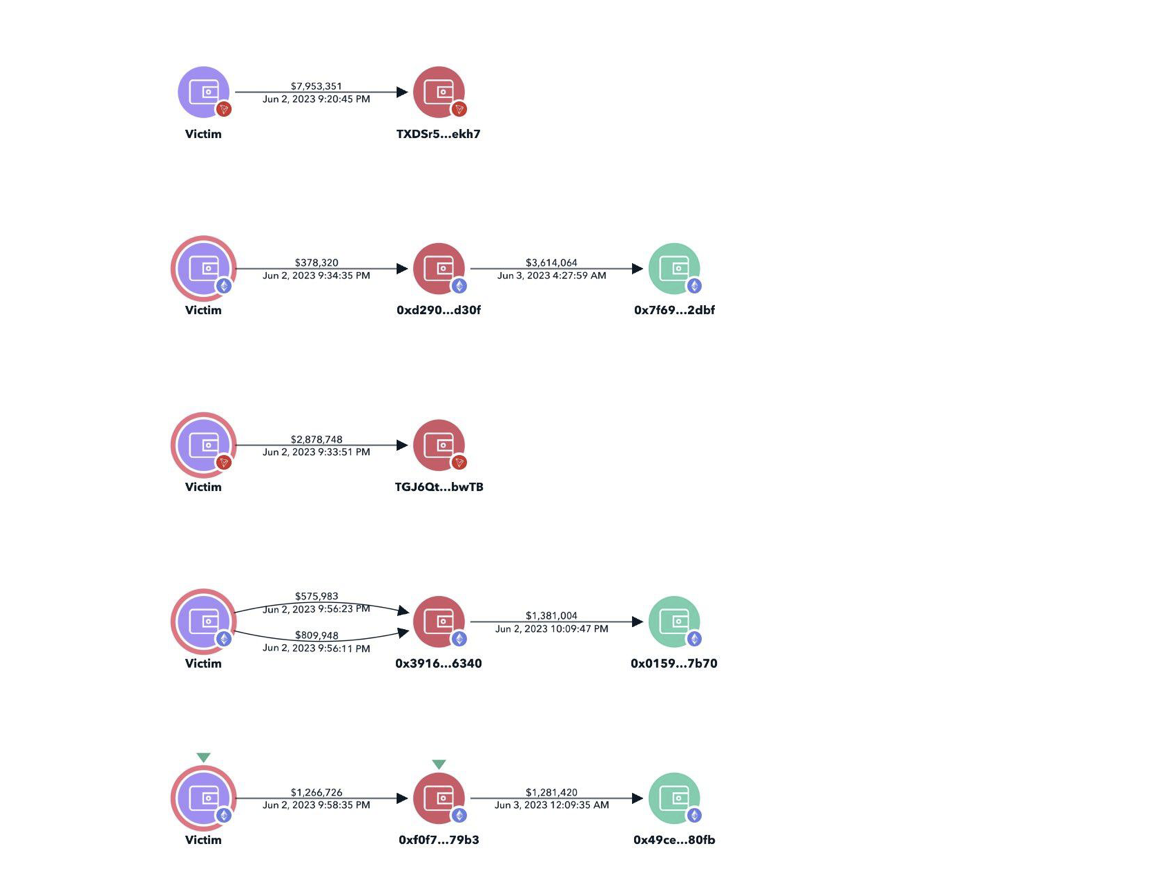
An image shared by ZachXBT on Twitter showcases his investigation into Atomic Wallet’s hack, offering further evidence of the breach.
Atomic Wallet has a user base of over 5 million individuals worldwide. In an interview, a long-time user named Emre, who happens to be a cybersecurity professional, shared his experience as a victim of a security breach.
Emre expressed deep distress after losing nearly $1 million in crypto assets obtained from bug bounty programs. The stolen tokens encompass Bitcoin (BTC), Dogecoin (DOGE), Litecoin (LTC), Ether (ETH), USDT, USD Coin (USDC), BNB, and Polygon (MATIC).
Emre highlighted the lack of concrete updates from Atomic Wallet regarding the incident. While the company claims to be investigating the matter, victims like Emre are still awaiting tangible progress. The funds stored in Atomic Wallet were intended for the establishment of…
Philadelphia Inquirer cyberattack remains under investigation
/in Internet Security
The Philadelphia Inquirer and outside cybersecurity experts have yet to determine the full extent of a cyberattack on the news organization last week, but the disruption won’t affect coverage of the hotly contested mayoral primary election Tuesday.
Lisa Hughes, The Inquirer’s publisher and chief executive, declined to say how seriously the cyberattack affected The Inquirer’s systems while the investigation continues. The attack prevented the publication of the regular Sunday print edition; subscribers received the early edition composed on Friday evening.
The attack is The Inquirer’s most significant publication disruption since a blizzard in 1996. With Inquirer offices closed as a precaution, staffers worked from home Monday as they did through the pandemic. But this time, they had to use workarounds to access publishing software and business systems. The Inquirer published a print edition Monday, but without classified ads, including death notices, which are expected to return to the newspaper Wednesday.
News staffers covering Tuesday’s election will work together at a temporary newsroom in Center City. The cyberattack affected internet servers and the effort to restore them requires systems to intermittently be turned off, Hughes said. The newsroom is expected to reopen Wednesday.
The cyberattack gained international attention, with CNN, Fortune, the New York Times, Associated Press, and the Guardian reporting on the news.
» READ MORE: The Philadelphia Inquirer’s operations continue to be disrupted by a cyber incident
Who committed the attack, how they accessed The Inquirer’s systems, what was targeted, and whether this was a result of ransomware remained unanswered. News organizations, including the Los Angeles Times and the Guardian have been victims of ransomware, software that freezes systems until the organization pays the perpetrators, in recent years.
Hughes declined to say Monday whether The Inquirer received a ransom demand or whether the individual or group responsible for the attack contacted the news organization.
The Inquirer notified the FBI of the attack, Hughes said. The federal law enforcement agency has said it typically does conduct an…
TUSD provides update on ransomware attack investigation
/in Internet Security
TUCSON, Ariz. (KGUN) — Tucson Unified School District has released a statement regarding the ransomware attack from January 30 which affected their network.
The district has emphasized its commitment to transparency and the communication of accurate and verifiable information to its employees and families, especially in emergency situations.
RELATED: New report finds 16,000 social security numbers and birth dates from TUSD on the dark web
Since the attack, TUSD has spoken with its staff members on a number of occasions, with the most recent being a letter from the district superintendent on March 31.
The district has been working closely with the Arizona Risk Retention Trust, their insurance carrier, and Packet Watch, a leading expert in cyberattack restoration and investigative efforts. They have also hired a group from ARETE Cyber Risk Management to review data that may have been hacked.
According to the statement, TUSD had several layers of system security in place before the cyberattack, and additional measures were taken after the attack to further increase security, including enabling multi-factor authentication for internal and external system access and the installation of the CrowdStrike Falcon platform.
The district confirms that a large amount of sensitive and confidential employee data has been accessed and taken, as noted in their March 31 letter to employees. However, the cyber-security forensic experts are still working to confirm the accuracy of any personal and confidential information that has been shared or published online.
The investigation requires the team to review tens of thousands of documents and files at a time and determine if each file can be connected to a current or former TUSD employee, parent, or student.
As a result, the district has not yet made any further statements about the validity of any district information that may have been posted on the dark web.
TUSD is encouraging its employees and families to keep a close eye on all banking information, accounts, and credit-related information.
Any affected workers will get a personal message from the district if the investigation finds that private information was exposed.
Below is the full statement…



