New attack steals e-mail decryption keys by capturing computer sounds
Computer scientists have devised an attack that reliably extracts secret cryptographic keys by capturing the high-pitched sounds coming from a computer while it displays an encrypted message.
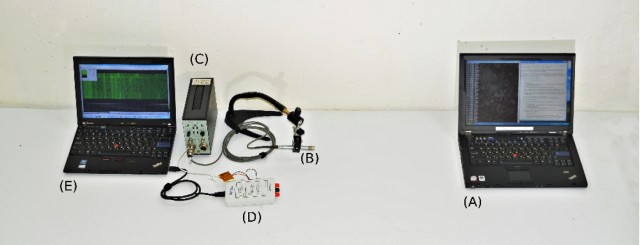
The technique, outlined in a research paper published Wednesday, has already been shown to successfully recover a 4096-bit RSA key used to decrypt e-mails by GNU Privacy Guard, a popular open source implementation of the OpenPGP standard. Publication of the new attack was coordinated with the release of a GnuPG update rated as “important” that contains countermeasures for preventing the attack. But the scientists warned that a variety of other applications are also susceptible to the same acoustic cryptanalysis attack. In many cases, the sound leaking the keys can be captured by a standard smartphone positioned close to a targeted computer as it decrypts an e-mail known to the attackers.
“We devise and demonstrate a key extraction attack that can reveal 4096-bit RSA secret keys when used by GnuPG running on a laptop computer within an hour by analyzing the sound generated by the computer during decryption of chosen ciphertexts,” the researchers wrote. “We demonstrate the attack on various targets and by various methods, including the internal microphone of a plain mobile phone placed next to the computer and using a sensitive microphone from a distance of four meters [a little more than 13 feet].”
Read 6 remaining paragraphs | Comments
![]()










