Prominent Sacramento law firm sues for $1 million after falling prey to ransomware attack
A prominent Sacramento law firm that represents police officers and sheriff’s deputies in the capital region is suing a computer firm for more than $1 million alleging that, after hiring the company to provide cybersecurity, the law firm was hit with a ransomware attack.
The Mastagni Holstedt law firm filed the suit in Sacramento Superior Court this week against Lantech LLC, claiming that because of the cyberattack last year, Mastagni Holstedt was forced to pay a ransom to regain access to its data.
An office manager at Lantech who would not give her name Wednesday morning declined to comment when reached by phone, saying she knew nothing about the suit, which names Lantech, former Lantech owner Terry Berg and backup computer data storage company Acronis Inc.
Lantech did not respond to a subsequent email request for comment, and Acronis denied any responsibility for the cyberattack.
Law firm founder Davis Mastagni also did not respond to a request for comment.
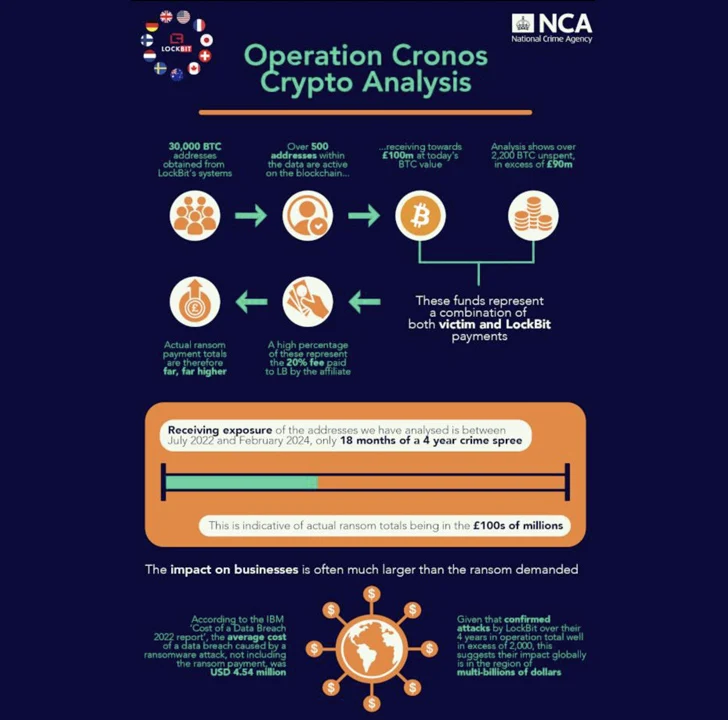
The lawsuit alleges the attack came from a group known as “Black Basta,” a Russian-speaking group first detected in early 2022 that has been blamed for hundreds of ransomware attacks that have resulted in payments of more than $100 million by firms seeking to retrieve data.
“In its first two weeks alone, at least 20 victims were posted to its leak site, a Tor site known as Basta News,” according to a March 2023 “threat profile” by the U.S. Health and Human Services Department’s Office of Information Security. “It exclusively targets large organizations in the construction and manufacturing industries, but was also observed to target other critical infrastructure, including the health and public health sector.
“While primarily targeting organizations within the United States, its operators also expressed interest in attacking other English-speaking countries’ organizations in Australia, Canada, New Zealand, and the United Kingdom. Threat actors that used the ransomware have additionally impacted organizations based in the United States, Germany, Switzerland, Italy, France, and the Netherlands.”
The group has extorted at least $107 million in bitcoin from targets, according to a November report by Reuters news…