Hackers use Royal Family website to promote links to porn and casinos | UK News
The Royal Family’s website is being used by ‘Black Hat SEO’ hackers to promote thousands of links to pornography and other adult content.
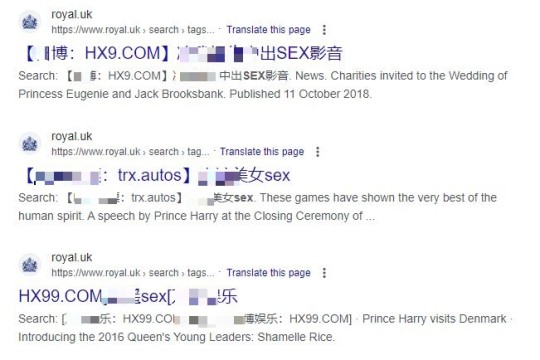
Google is investigating after the prestigious royal.uk address was hijacked by spammers posting blurbs in a mixture of Mandarin Chinese and English.
Searches on the engine show that the official URL has been ‘malformed’ to link to explicit and potentially harmful content elsewhere on the web.
The majority advertise casino and gambling sites while hundreds link to pornography in the attempt to boost search engine optimisation (SEO).
The royals are among the victims of a practice whereby hackers use the online presence of reputable organisations to promote grubby content and increase their rankings in valuable search engine listings.
Although there is no inappropriate material visible on the royal website itself, the rogue links show up in Google searches. The official title complete with the Royal Coat of Arms appears above each result.
The spammers are thought to have tampered with the royal domain’s metadata — the embedded words and descriptive data which tell people what the content is about. Crucially, it helps search engines understand and index web pages accurately.
Adrianus Warmenhoven, a cybersecurity advisor at NordVPN, said: ‘By Royal Appointment is one of the most valuable endorsements that a company can receive, and these hackers have found a way to gain credit via the back door. It looks like they have managed to insert some malicious code in the metadata of the official Royal Family website and hidden rogue links to all sorts of unsavoury pages.
‘Hackers often use phishing attacks to grab passwords, which can let them log in and edit the website metadata.
‘Visitors to the website shouldn’t stumble across these links, but scammers are benefiting from the association with one of the world’s most prestigious domain names.’
Other trusted domain names have been used to promote and…