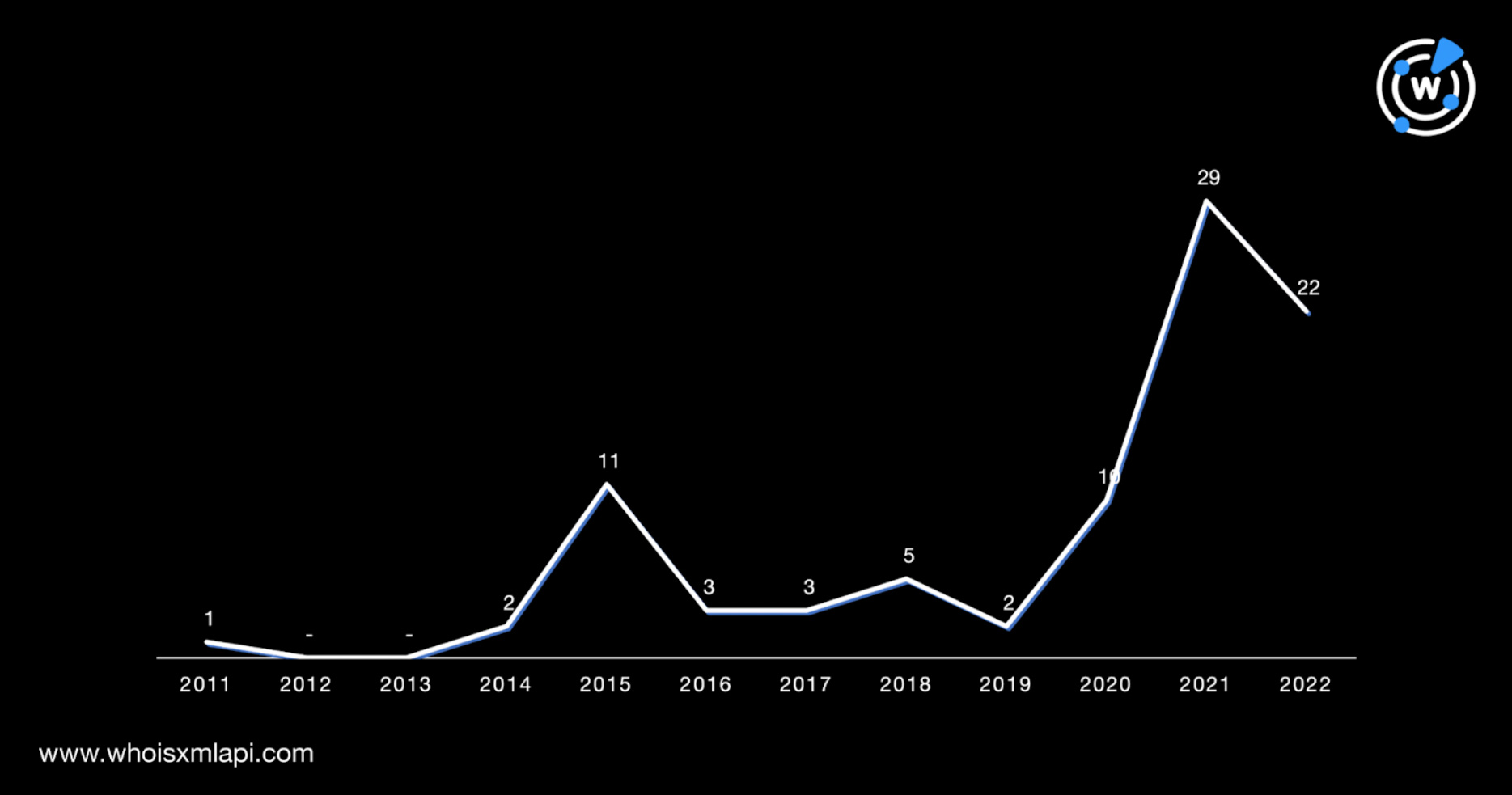
Live Updates: Xi Warns of ‘Dangerous Storms’ Facing China
Xi Jinping Thought is ubiquitous in China, detailed in everything from textbooks to collections of Mr. Xi’s writings, from dedicated research centers to apps for studying his works.
In China, having a political philosophy named after a leader carries enormous significance. For Mr. Xi, it is a core expression of his expanding power. At his speech opening the Communist Party’s congress in Beijing on Sunday, he said that “fully implementing” his thought was a key theme.
During the meeting this week, China’s political elite are expected to further elevate the status of the political doctrine — and by extension, Mr. Xi’s authority.
The party is likely to amend its constitution to change the name of the theory, officially known as Xi Jinping Thought on Socialism With Chinese Characteristics for a New Era.
“‘Xi Jinping Thought on Socialism With Chinese Characteristics for a New Era’ is a crown that’s too heavy to wear,” said David Bandurski, the director of the China Media Project, a research organization. “So, he wants a crown he can actually wear.”
Many analysts expect the phrase to be shortened to Xi Jinping Thought. That would make it a “pithy, direct, powerful signal” of his authority, Mr. Bandurski said.
Mr. Xi already had the full phrase inserted into the party charter in 2017. That put Mr. Xi above his most recent predecessors, Hu Jintao and Jiang Zemin, whose own ideological contributions, while mentioned in the same document, don’t carry their names in the titles. It even vaulted him above Deng Xiaoping, whose eponymous input is labeled a “theory.”
The ideology is more than an empty celebration of Mr. Xi. Xi Jinping Thought is a framework for China’s governance and a guide for what it will do under his continuing leadership.
The goal of Mr. Xi’s ideology is to cement the Communist Party’s role as China’s governing body, with a single strong leader — Mr. Xi himself — at the top, dispensing with the more collective leadership style of his recent predecessors.
Mr. Xi has escalated a crackdown on corruption, a widely popular effort that also helps command cadres’ loyalty to him and ensures that the party, not the public at large, decides…