Atomic Wallet Hack Exposes $35 Million Crypto Asset Theft – An In-depth Look at the Aftermath and Ongoing Investigation
Join Our Telegram channel to stay up to date on breaking news coverage
The Atomic Wallet hack has shaken the crypto community, causing substantial user losses and prompting an urgent investigation. Here’s a closer look at the aftermath, recovery efforts, and the wider landscape of cryptocurrency breaches, along with Atomic Wallet’s response to the incident.
Atomic Wallet Hack Reveals $35 Million in Crypto Asset Theft
An analysis conducted by on-chain investigator ZachXBT reveals that Atomic Wallet users have suffered crypto asset theft amounting to at least $35 million since June 2. Among these losses, the five largest account for $17 million.
After the attack, Atomic Wallet took to Twitter to inform users that they were actively conducting an investigation into the cause of the incident. Troubling accounts have surfaced, revealing instances of token losses, erasure of transaction histories, and even the outright theft of entire crypto portfolios.
ZachXBT, a pseudonymous Twitter user known for tracking stolen crypto funds and aiding hacked projects, independently conducted an investigation. According to ZachXBT’s findings, the largest victim lost $7.95 million in Tether (USDT). ZachXBT commented that the total amount stolen could potentially exceed $50 million as more victims continue to be discovered.
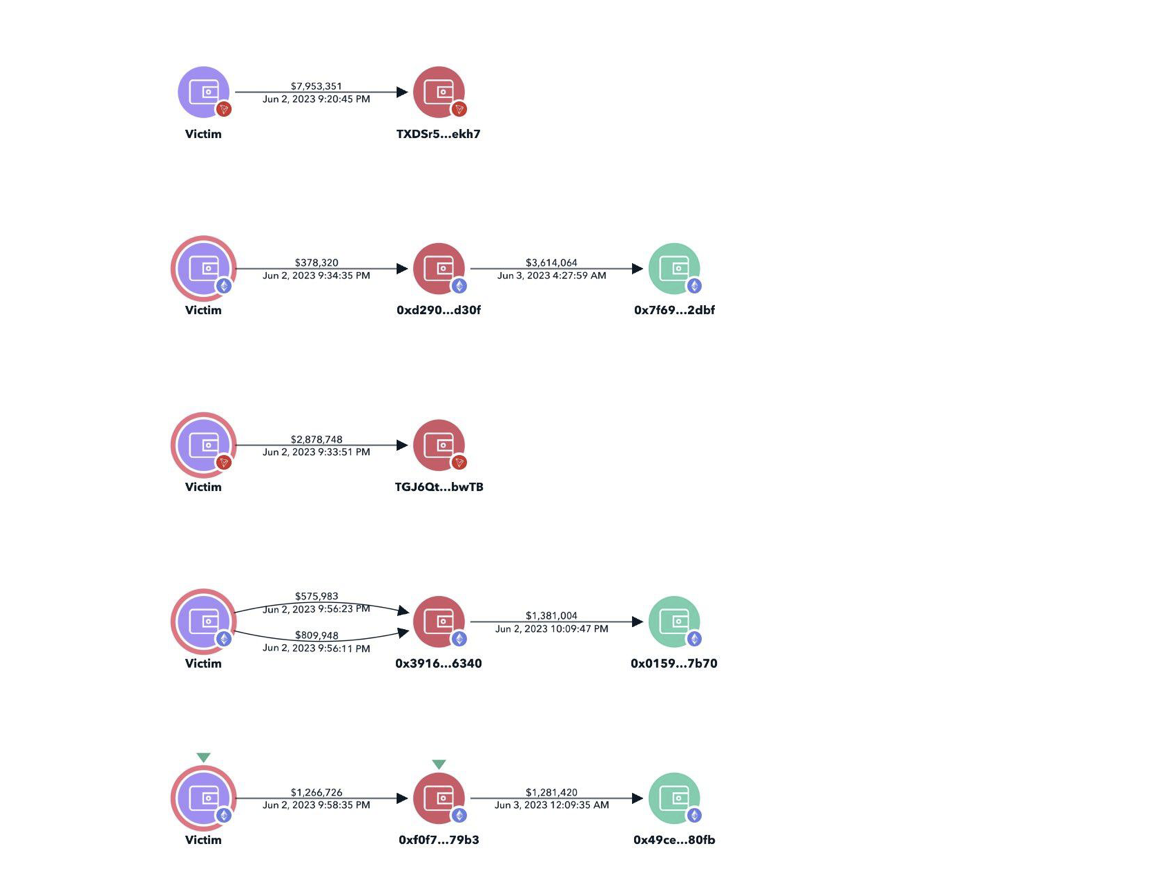
An image shared by ZachXBT on Twitter showcases his investigation into Atomic Wallet’s hack, offering further evidence of the breach.
Atomic Wallet has a user base of over 5 million individuals worldwide. In an interview, a long-time user named Emre, who happens to be a cybersecurity professional, shared his experience as a victim of a security breach.
Emre expressed deep distress after losing nearly $1 million in crypto assets obtained from bug bounty programs. The stolen tokens encompass Bitcoin (BTC), Dogecoin (DOGE), Litecoin (LTC), Ether (ETH), USDT, USD Coin (USDC), BNB, and Polygon (MATIC).
Emre highlighted the lack of concrete updates from Atomic Wallet regarding the incident. While the company claims to be investigating the matter, victims like Emre are still awaiting tangible progress. The funds stored in Atomic Wallet were intended for the establishment of…



