North American Orgs Hit With an Average of 497 Cyberattacks per Week
New data released this week confirms what numerous others have reported as a massive surge in attacks against organizations worldwide since the COVID-19 pandemic forced dramatic changes to workplace and operational environments.
A recent analysis of threat activity by Check Point Software Technologies shows that the average number of weekly attacks on organizations globally so far this year is 40% higher than the average before March 2020, when the first pandemic-related changes went into effect. In the US, the average increase is even higher, at 53%.
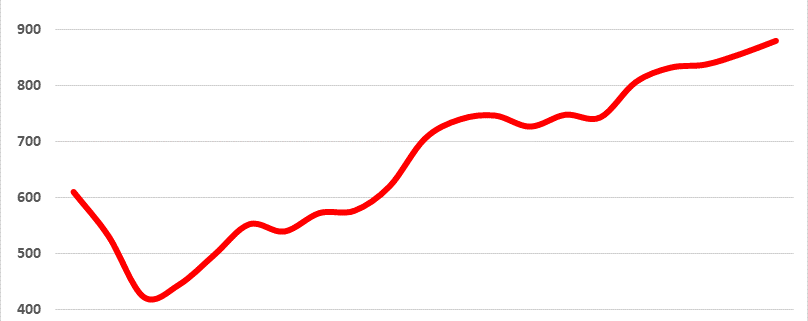
Check Point’s data shows there were more average weekly attacks in September 2021 than any time since January 2020. In fact, the 870 attacks per organization globally per week that Check Point counted in September this year was double the average in March 2020.
In terms of of raw attack volume, companies and other organizations in Africa experienced more weekly attacks this year — 1,615 — than any other region. Though North American companies experienced the highest growth in attack volumes, the actual number of attacks per week was lower, at 497 per organization.
As has been the case for some time now, some industry sectors were more heavily targeted than others. Education and research organizations, for instance, witnessed a 60% increase in attacks from 2020 and currently average 1,468 attacks per week.
Government and military entities, with an average of 1,082 weekly attacks, were the next most highly attacked, while healthcare organizations are currently dealing with some 752 attacks per week on average — or a 55% increase from last year.
Check Point’s data is similar to data from other vendors that have noted a sharp increase in attacks targeting these sectors. For instance, the need for school districts to support new distance learning models in the wake of the pandemic has made them even bigger targets for ransomware operators than they were already. Over the past year, there have been numerous reports of ransomware attacks disrupting
attempts to deliver classes online and often forcing school districts to deal with huge ransom demands.
Similarly, hospitals and healthcare networks that are central to fighting the…