Phishing ai danni di clienti Booking.com e settore turistico: come difendersi
Nel corso delle ultime settimane, il settore turistico è stato preso di mira da una sofisticata campagna di furto di informazioni che ha colpito hotel, siti di prenotazione e agenzie di viaggio.
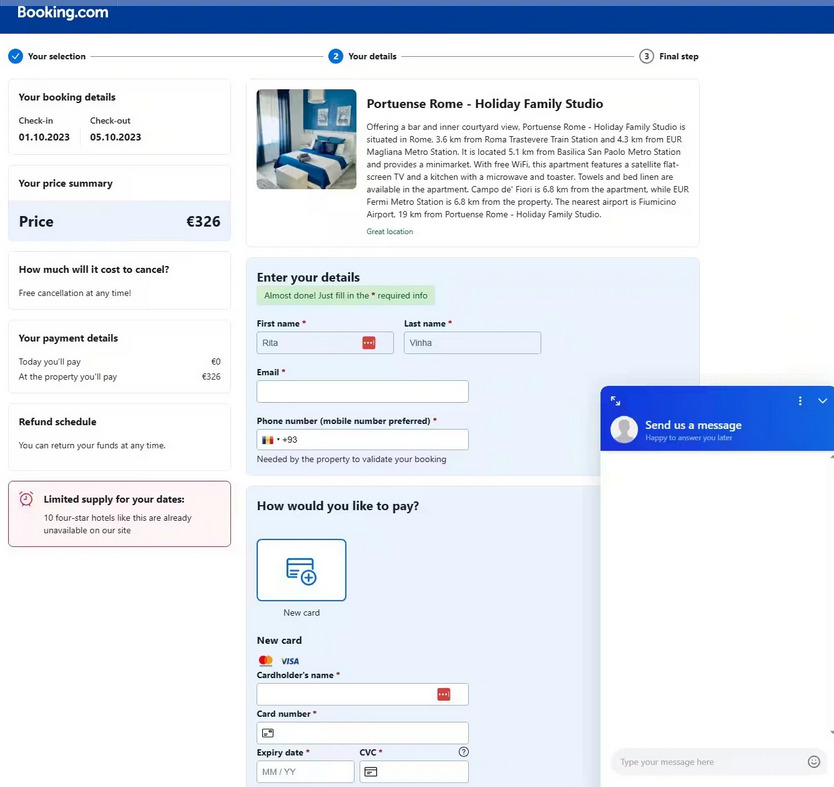
I ricercatori di sicurezza hanno scoperto che i criminal hacker utilizzano un approccio indiretto e una falsa pagina di pagamento di Booking.com per ottenere un accesso illimitato ai dati finanziari dei clienti.
La falsa pagina web di Booking.com usata come esca
La campagna, definita “Phishing di Livello Successivo” dai ricercatori di cyber security, è stata scoperta da Perception Point, un’azienda specializzata nella sicurezza informatica. La campagna inizia con una semplice richiesta di prenotazione o si riferisce a una prenotazione già esistente.
Abilitazione al cloud: migrazione, gestione delle applicazioni e sicurezza. Rendi più potente l’IT
Una volta stabilito il contatto con l’hotel o l’agenzia di viaggi, gli attaccanti trovano una scusa, come una presunta condizione medica o una richiesta speciale da parte di un viaggiatore, per inviare documenti importanti tramite una URL appositamente disegnata.
Tuttavia, l’URL in realtà conduce a un malware progettato per operare in modo invisibile, rubando dati sensibili come le credenziali di accesso e le informazioni finanziarie dei clienti.
Ciò che rende questa campagna particolarmente pericolosa è il suo approccio successivo.
Secondo un rapporto recente di Akamai, un’azienda Internet specializzata in servizi di cloud e sicurezza, una volta che il malware è stato eseguito con successo sull’hotel o l’agenzia di viaggi, gli attaccanti ottengono accesso diretto alla messaggistica con i clienti legittimi. Questo canale di comunicazione diretto e affidabile consente loro di inviare messaggi di phishing mascherati da richieste legittime provenienti dall’hotel o dalla società di prenotazione compromessa.
Il messaggio richiede ulteriori verifiche sulla carta di credito e si basa su tecniche di ingegneria sociale avanzate. Shiran Guez, Senior Manager della Sicurezza Informatica presso Akamai, ha sottolineato che il messaggio è scritto in modo professionale e si basa sulle autentiche interazioni dell’hotel con i suoi ospiti,…