Ransomware group threatens to leak Stanford police data
Notorious ransomware gang ‘Akira’ listed Stanford University on the darknet as the target of a ransomware attack on Friday morning. Screenshots of the listing were shared on other parts of the internet, including the r/stanford subreddit and on X (formerly Twitter) by cyber risk analyst Brett Callow.
University spokesperson Luisa Rapport confirmed “this is the same as the SUDPS cybersecurity incident” previously covered by The Daily.
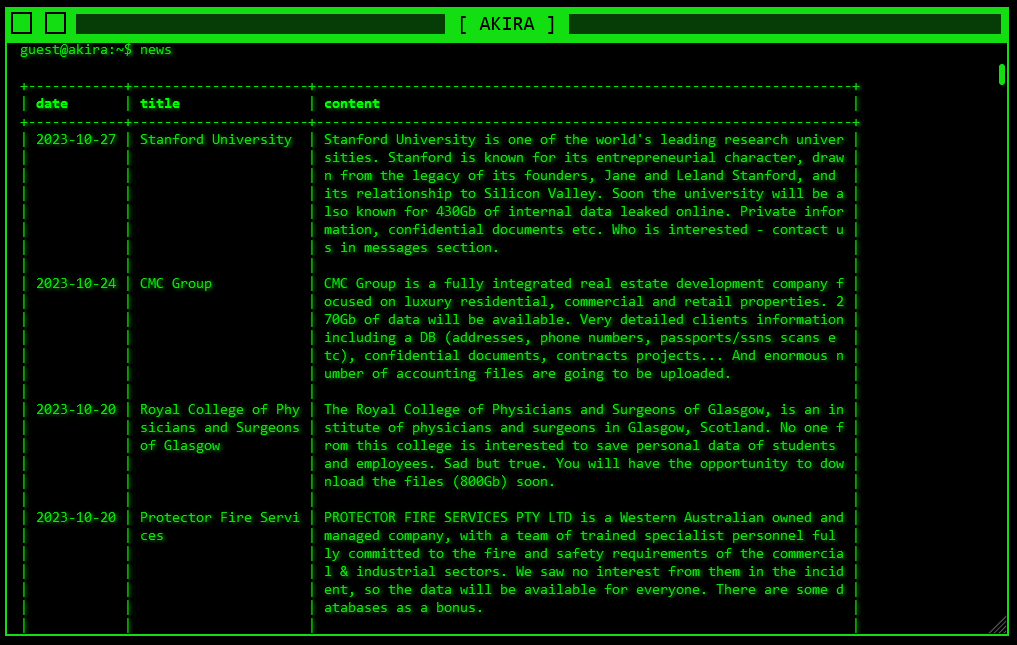
Akira claims to hold 430 gigabytes of internal data, including private information and confidential documents. They threatened to leak the information online if the University did not pay an unspecified ransom. The Stanford University Department of Public Safety processes and stores data on personnel, case reports, risk evaluations and crime involving students, faculty and other community members. It is unclear at this point how much of this data was lost or encrypted by this ransomware.
The University wrote in a Friday statement that “there is no indication that the incident affected any other part of the university, nor did it impact police response to emergencies.” According to the statement, “the investigation is ongoing and once it is completed, we will act accordingly and be able to share more information with the community.”
The Akira listing describes Stanford as “known for its entrepreneurial character.” The group threatened that, “Soon the university will be also known for 430Gb of internal data leaked online. Private information [and] confidential documents.”
Chris Hoofnagle, law professor and director of the Center for Law & Technology at the University of California, Berkeley, wrote to The Daily that attackers interested in police entities are sometimes “a nation state or organized crime” group.
“The first steps of identifying the scope of the breach can be quite expensive and time consuming. Almost all entities hire outside forensic firms to do the analysis,” Hoofnagle wrote.
He wrote it was “best practice” to limit information until there was information on the full scope of the breach and the network was secure. “Institutions do not want to get into a drip situation where they notify…