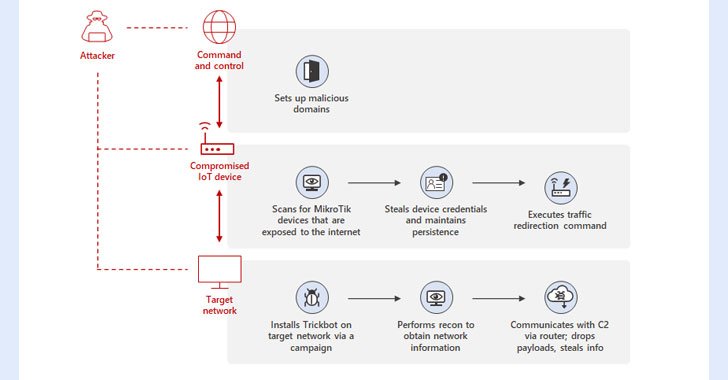
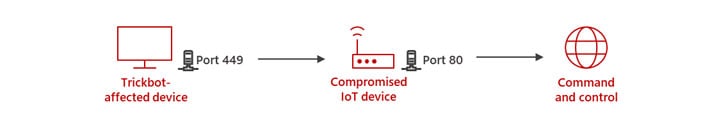
‘Black Proxies’ Enable Threat Actors to Conduct Malicious Activity
Threat actors have been spotted using criminal proxy networks to obfuscate their illegal activities by hiding behind hijacked IP addresses and using the same to create an appearance of legitimacy.
The findings come from security researchers at DomainTools, who have said that while these networks were initially used as part of botnets, their lucrative nature has turned them into their own criminal enterprises.
Describing the new threat in an advisory published on Thursday, the DomainTools team said it spotted a new and particularly dangerous proxy service called ‘Black Proxies,’ which is being marketed to other cyber-criminals for its reliability, scope and vast number of IP addresses.
“Black Proxies market themselves as having over 1,000,000 residential and other proxy IP addresses ‘from all around the world.’ The scope and scale of these new offerings show just how large their claimed pool of IP space is,” DomainTools wrote.
“Upon further examination through the service, their pool of IP addresses listed in fall of 2022 ‘online’ comes in at just over 180,000 IPs, which is still a factor larger than the traditional services based on other types of tactics and botnets.”
According to the advisory, the Black Proxies’ scale is significant because of not only their focus on both the traditional forms of IP proxying but also their use of compromised websites for their services.
“Ultimately, in the cybercrime ecosystem, there are a host of specialized services designed to enable malicious activity,” reads the report.
The researchers also added that understanding these newer malicious proxy services and how they facilitate the efforts of other cyber-criminals is critical in order to combat them.
“For defenders looking to protect their organizations and users from these types of proxy network services, the key is to focus on defense in depth, applying different detection methods to help identify anomalous and potentially malicious behavior,” concluded the report.
Malicious domains were also at the center of a typosquat campaign uncovered in October, which highlighted attacks targeting Windows and Android users mimicking 27 brands.