No SOCKS, No Shoes, No Malware Proxy Services! – Krebs on Security
With the recent demise of several popular “proxy” services that let cybercriminals route their malicious traffic through hacked PCs, there is now something of a supply chain crisis gripping the underbelly of the Internet. Compounding the problem, several remaining malware-based proxy services have chosen to block new registrations to avoid swamping their networks with a sudden influx of customers.
Last week, a seven-year-old proxy service called 911[.]re abruptly announced it was permanently closing after a cybersecurity breach allowed unknown intruders to trash its servers and delete customer data and backups. 911 was already akin to critical infrastructure for many in the cybercriminal community after its top two competitors — VIP72 and LuxSocks — closed or were shut down by authorities over the past 10 months.
The underground cybercrime forums are now awash in pleas from people who are desperately seeking a new supplier of abundant, cheap, and reliably clean proxies to restart their businesses. The consensus seems to be that those days are now over, and while there are many smaller proxy services remaining, few of them on their own are capable of absorbing anywhere near the current demand.
“Everybody is looking for an alternative, bro,” wrote a BlackHatForums user on Aug. 1 in response to one of many “911 alternative” discussion threads. “No one knows an equivalent alternative to 911[.]re. Their service in terms of value and accessibility compared to other proxy providers was unmatched. Hopefully someone comes with a great alternative to 911[.]re.”
NEW SOCKS, SAME OLD SHOES
Among the more frequently recommended alternatives to 911 is SocksEscort[.]com, a malware-based proxy network that has been in existence since at least 2010. Here’s what part of their current homepage looks like:
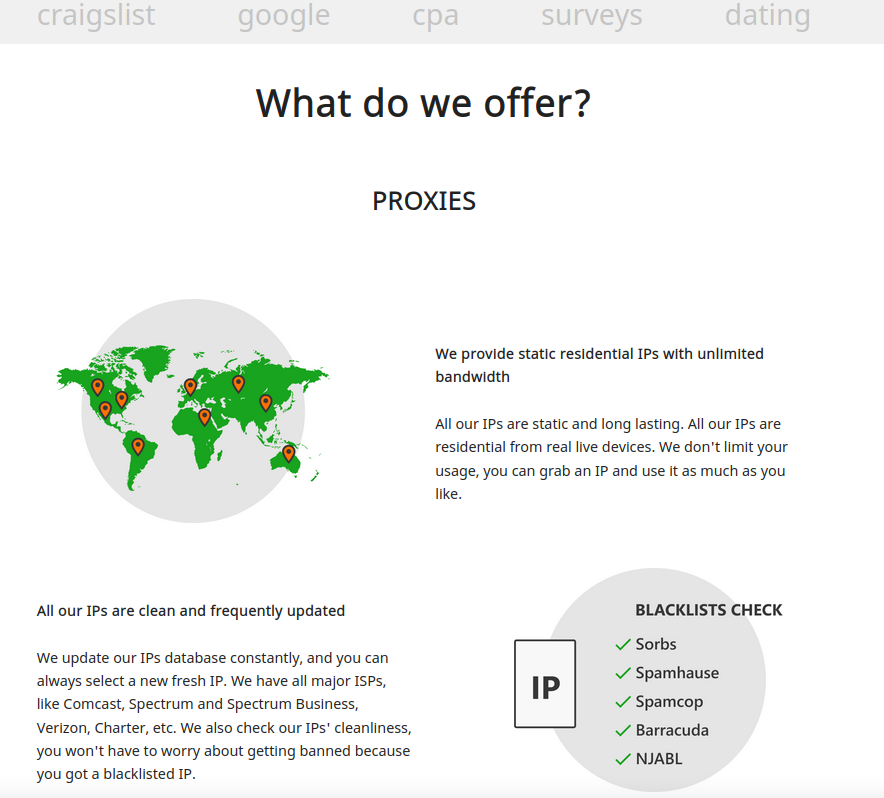
The SocksEscort home page says its services are perfect for people involved in automated online activity that often results in IP addresses getting blocked or banned, such as Craigslist and dating scams, search engine results manipulation, and online surveys.
But faced with a deluge of new signups in the wake of 911’s implosion, SocksEscort was among the…