QNAP Warns of OpenSSL Infinite Loop Vulnerability Affecting NAS Devices
Taiwanese company QNAP this week revealed that a selected number of its network-attached storage (NAS) appliances are affected by a recently-disclosed bug in the open-source OpenSSL cryptographic library.
“An infinite loop vulnerability in OpenSSL has been reported to affect certain QNAP NAS,” the company said in an advisory published on March 29, 2022. “If exploited, the vulnerability allows attackers to conduct denial-of-service attacks.”
Tracked as CVE-2022-0778 (CVSS score: 7.5), the issue relates to a bug that arises when parsing security certificates to trigger a denial-of-service condition and remotely crash unpatched devices.
QNAP, which is currently investigating its line-up, said it affects the following operating system versions –
- QTS 5.0.x and later
- QTS 4.5.4 and later
- QTS 4.3.6 and later
- QTS 4.3.4 and later
- QTS 4.3.3 and later
- QTS 4.2.6 and later
- QuTS hero h5.0.x and later
- QuTS hero h4.5.4 and later, and
- QuTScloud c5.0.x
To date, there is no evidence that the vulnerability has been exploited in the wild. Although Italy’s Computer Security Incident Response Team (CSIRT) released an advisory to the contrary on March 16, the agency clarified to The Hacker News that it has “updated the alert with an errata corrige.”
The advisory comes a week after QNAP released security updates for QuTS hero (version h5.0.0.1949 build 20220215 and later) to address the “Dirty Pipe” local privilege escalation flaw impacting its devices. Patches for QTS and QuTScloud operating systems are expected to be released soon.
A new ransomware gang known as “DeadBolt” is targeting QNAP NAS customers using an alleged zero-day vulnerability.
The attacks have impacted vulnerable QNAP network-attached storage (NAS) devices exposed to the internet. DeadBolt, the ransomware at the center, appears to be a new gang and ransomware strain, as initial reports came early this week.
Taiwanese hardware vendor QNAP published a blog Wednesday to confirm the ongoing attacks and urge users to secure their devices. Specifically, the blog provides instructions to users on how to check whether an NAS device is accessible from an external IP address, as well as how to change this by disabling port forwarding and Universal Plug and Play functionality.
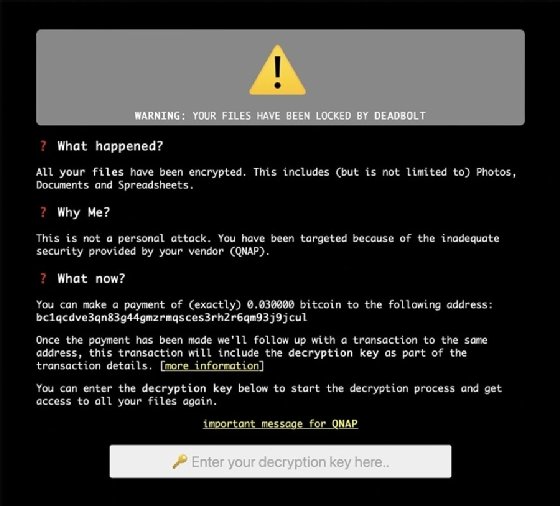
“DeadBolt has been widely targeting all NAS exposed to the Internet without any protection and encrypting users’ data for Bitcoin ransom,” the post read. “QNAP urges all QNAP NAS users to follow the security setting instructions below to ensure the security of QNAP NAS and routers, and immediately update QTS to the latest available version.”
According to ransom notes posted by alleged victims and security researchers, DeadBolt is demanding 0.03 bitcoin from victims (currently valued at just over $1,100 USD).
“This is not a personal attack. You have been targeted because of the inadequate security provided by your vendor (QNAP),” the ransom note read. QNAP NAS users have dealt with other ransomware variants in recent weeks and months, including variants Qlocker and eCh0raix.
The ransom note includes an additional note from DeadBolt to QNAP, claiming the threat actor is targeting users via a zero-day vulnerability and that in order to receive vulnerability details and a universal decryption key, the vendor must send 50 bitcoin (almost $2,000,000 as of this writing) to the threat actor. Alternatively, QNAP can send 5 bitcoin (approximately $190,000 as of this writing) to receive only the vulnerability details.
Numerous victim reports can be seen on multiple fronts, including the QNAP NAS Community Forum and r/QNAP on Reddit.
“Hi, my QNAP NAS drive just got attacked by a [ransomware]…




