Hackers Exploited Zero-Day RCE Vulnerability in Sophos Firewall — Patch Released
Security software company Sophos has released a patch update for its firewall product after it was discovered that attackers were exploiting a new critical zero-day vulnerability to attack its customers’ network.
The issue, tracked as CVE-2022-3236 (CVSS score: 9.8), impacts Sophos Firewall v19.0 MR1 (19.0.1) and older and concerns a code injection vulnerability in the User Portal and Webadmin components that could result in remote code execution.
The company said it “has observed this vulnerability being used to target a small set of specific organizations, primarily in the South Asia region,” adding it directly notified these entities.
As a workaround, Sophos is recommending that users take steps to ensure that the User Portal and Webadmin are not exposed to WAN. Alternatively, users can update to the latest supported version –
- v19.5 GA
- v19.0 MR2 (19.0.2)
- v19.0 GA, MR1, and MR1-1
- v18.5 MR5 (18.5.5)
- v18.5 GA, MR1, MR1-1, MR2, MR3, and MR4
- v18.0 MR3, MR4, MR5, and MR6
- v17.5 MR12, MR13, MR14, MR15, MR16, and MR17
- v17.0 MR10
Users running older versions of Sophos Firewall are required to upgrade to receive the latest protections and the relevant fixes.
The development marks the second time a Sophos Firewall vulnerability has come under active attacks within a year. Earlier this March, another flaw (CVE-2022-1040) was used to target organizations in the South Asia region.
Then in June 2022, cybersecurity firm Volexity shared more details of the attack campaign, pinning the intrusions on a Chinese advanced persistent threat (APT) known as DriftingCloud.
Sophos firewall appliances have also previously come under attack to deploy what’s called the Asnarök trojan in an attempt to siphon sensitive information.
Zoom users on macOS are being told once again to update their copy of the video-conferencing software after a security hole was found that could be exploited by hackers.
At Defcon earlier this month, Mac security expert Patrick Wardle demonstrated a vulnerability in Zoom for macOS’s auto-update feature that could allow an attacker to “trivially escalate their privileges to root.”
Wardle found a method by which malicious hackers could trick Zoom’s auto-update feature into downgrading the software to an earlier (and hence less-secure) version of Zoom, or even install an entirely different program in its place – with root access to the entire Mac computer.
To its credit, Zoom issued a security update in response to Wardle’s findings – and told Mac users to update their systems to Zoom version 5.11.5.
Wardle posted on Twitter that he was impressed with Zoom’s “(incredibly) quick fix.”
However, it has since turned out that Zoom’s initial fix to the security vulnerability was not good enough.
Another Mac security researcher, Csaba Fitzl, looked at Zoom’s patch and found it was incomplete, allowing him to bypass the fix and still exploit the vulnerability. And if a security researcher like Fitzl can find a way to exploit a weakness in Zoom’s security patch, so could a malicious hacker.
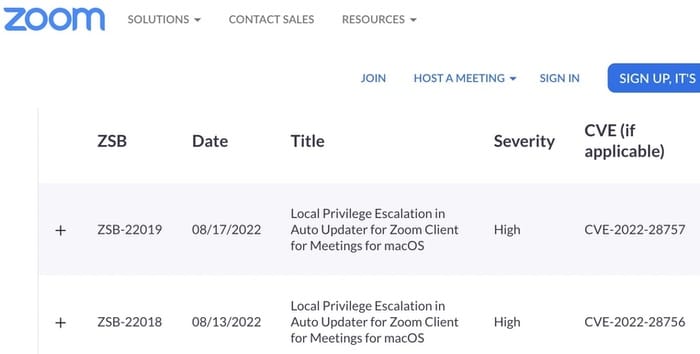
This, of course, has meant that Zoom has had to release a security patch for its previous (flawed) security patch.
As you can see on Zoom’s list of security bulletins, the fixes came in quick succession.
Zoom users on macOS would be wise to update their client to version 5.11.6 or later immediately. I wouldn’t recommend waiting for the auto-update feature to decide to look for an update. Instead, initiate a manual update by choosing the “Check for Updates…” menu option within Zoom.
The latest version of Zoom (containing all the current security updates) is also available from Zoom’s website at https://zoom.us/download









