Veeam’s New ‘Cyber Secure Program’ Teams Tech with Ransomware Response Experts — Virtualization Review
Veeam’s New ‘Cyber Secure Program’ Teams Tech with Ransomware Response Experts
Along with purpose-built technology to combat ransomware, Veeam Software’s new Cyber Secure Program also offers up a team of experts to help organizations wield that tech to fight threat actors.
“When there is an attack, customers are connected with Veeam’s dedicated Ransomware Response Team and the program offers post-incident support to enable rapid recovery,” said the specialist in data protection and ransomware recovery.
The three-pronged approach of Veeam Cyber Secure includes the expert help for secure design and implementation along with ransomware recovery support backed up by a recovery warranty for help in all three phases of an attack: pre-incident, during incident and post-incident.
The teams of experts include a dedicated support account manager and “Ransomware SWAT Team” to help with immediate action in case of a cyber incident
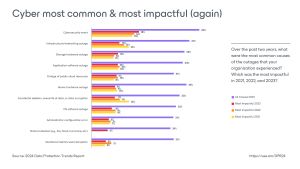
The new offering comes in the wake of the company’s 2024 Data Protection Report that revealed ransomware is still plaguing IT as the No 1. cause of server outages.
“Consider the past 12 months: 76 percent of organizations have been attacked at least once, with 26 percent reporting being attacked at least four times and only 13 percent believe they can recover successfully after an attack,” Veeam said. “It’s clear that organizations need a comprehensive cyber protection and support program, ultimately ensuring they are well-prepared when cyberattacks occur.”
A Jan. 31 news release further fleshed out the new program’s three key components.
- Confident Security: Attentive and dedicated design and implementation assistance to ensure Veeam best practices in securely implementing Veeam solutions to the highest security standards. Customers receive advanced seven-phase onboarding support and rigorous quarterly security…