Microsoft Warns of Hackers Using Google Ads to Distribute Royal Ransomware
A developing threat activity cluster has been found using Google Ads in one of its campaigns to distribute various post-compromise payloads, including the recently discovered Royal ransomware.
Microsoft, which spotted the updated malware delivery method in late October 2022, is tracking the group under the name DEV-0569.
“Observed DEV-0569 attacks show a pattern of continuous innovation, with regular incorporation of new discovery techniques, defense evasion, and various post-compromise payloads, alongside increasing ransomware facilitation,” the Microsoft Security Threat Intelligence team said in an analysis.
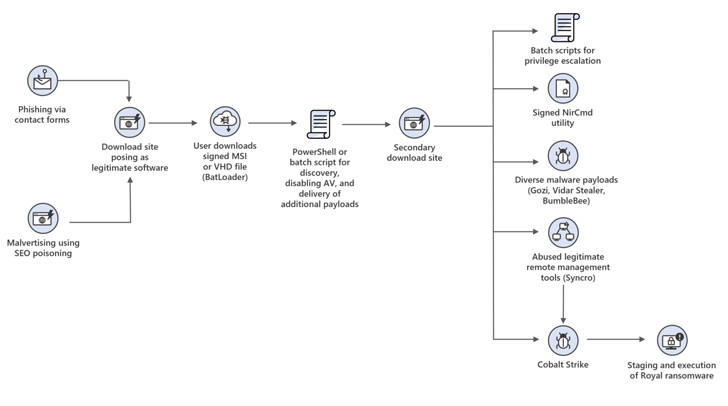
The threat actor is known to rely on malvertising to point unsuspecting victims to malware downloader links that pose as software installers for legitimate apps like Adobe Flash Player, AnyDesk, LogMeIn, Microsoft Teams, and Zoom.
The malware downloader, a strain referred to as BATLOADER, is a dropper that functions as a conduit to distribute next-stage payloads. It has been observed to share overlaps with another malware called ZLoader.
A recent analysis of BATLOADER by eSentire and VMware called out the malware’s stealth and persistence, in addition to its use of search engine optimization (SEO) poisoning to lure users to download the malware from compromised websites or attacker-created domains.
Alternatively, phishing links are shared through spam emails, fake forum pages, blog comments, and even contact forms present on targeted organizations’ websites.
“DEV-0569 has used varied infection chains using PowerShell and batch scripts that ultimately led to the download of malware payloads like information stealers or a legitimate remote management tool used for persistence on the network,” the tech giant noted.
“The management tool can also be an access point for the staging and spread of ransomware.”
Also utilized is a tool known as NSudo to launch programs with elevated privileges and impair defenses by adding registry values that are designed to disable antivirus solutions.
The use of Google Ads to deliver BATLOADER selectively marks a diversification of the DEV-0569’s distribution vectors, enabling it to reach more targets and deliver malware payloads, the company…


 Prince Edward, Duke of Kent has been Patron of BCS since 1979 and in 1982, BCS’ silver jubilee year, he became president of the organisation.
Prince Edward, Duke of Kent has been Patron of BCS since 1979 and in 1982, BCS’ silver jubilee year, he became president of the organisation.
 A growing concern for the British Royal Family are the threat from hackers and other cyber criminals who pose a security threat and it emerges that Queen Elizabeth has taken the decision to increase the royal’s cyber security.
A growing concern for the British Royal Family are the threat from hackers and other cyber criminals who pose a security threat and it emerges that Queen Elizabeth has taken the decision to increase the royal’s cyber security. 