BPUB customer concerned about ransomware, sees foreign logins to email
BROWNSVILLE, Texas (ValleyCentral) — Customers with the Brownsville Public Utility Board (BPUB) are growing concerned following the news of a ransomware attack, and one customer said she believes she is being affected by it.
A Brownsville PUB customer, that wishes to remain anonymous, reached out to ValleyCentral about texts and calls from unknown numbers asking to confirm her identity.
“I saw it and I thought nothing of it until I remembered that I saw your report on the news,” said the customer.
She said she believes the ransomware hack is related to what she experienced this week.
This customer added that she also noticed a foreign login to her email account from Moscow, Russia.
“I pay my parents’ account through my account. It has never happened before I’ve never had an issue,” said the customer. “So, I just started freaking out since then.”
However, the BPUB does not believe the ransomware attack is linked to what she is experiencing.
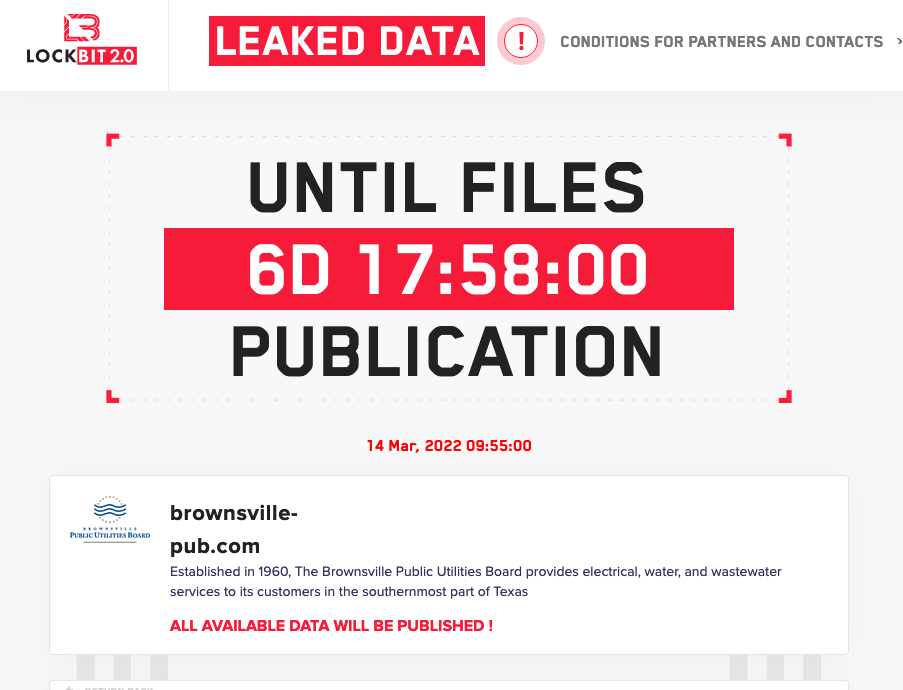
The BPUB says they still have an ongoing investigation and they can’t release too much of the details just yet. According to the ransomware website ‘Lockbit,’ the BPUB has until Monday to pay the ransom or information could be leaked.
“One of the things that we’re trying to find out, is what files if any were compromised,” said Ryan Greenfeld, the communications and public relations manager at BPUB.
Greenfeld did not specify whether BPUB would pay the ransom or not.
“Right now, our goals are to remove any infections from our systems, make sure all viruses are cleaned, and to make sure all internal data and functionality is restored,” said Greenfeld.
To better protect your information online:
- Use two-step authentication
- Do not open suspicious emails
- Do not click on unknown URL links
- Change your password every few months
ValleyCentral will continue following this developing story.