YouTube influencers selling VPNs may be a security issue

Whether you’re a keen YouTube streamer or you hop on the platform from time to time, it’s very likely you have come across several hosts advertising the best VPN service of the moment for top privacy and geo-blocking online.
From a niche tool targeting businesses and cybersecurity nerds, virtual private networks (VPNs) have seen a boom in usage among everyday users in the latest years. VPN popularity is indeed tangled up with the fact that today’s digital life—for better or worse—is getting more complex and central in our lives. Even so, influencers trying to convince their subscribers to make the purchase have inevitably been a big push for this growth—while getting their cut.
Nothing out of the ordinary that other companies don’t do, you might think. Yet, helping people to protect their most sensitive data involves way more responsibilities than recommending a new pair of shoes or a smartphone.
Recent research investigating influencer VPN ads might be more harmful than good after all, by “negatively influencing viewers’ mental models of internet safety.” We asked the main providers out there what they are doing—if anything—to prevent this from happening.
The risks of influencer VPN ads on YouTube
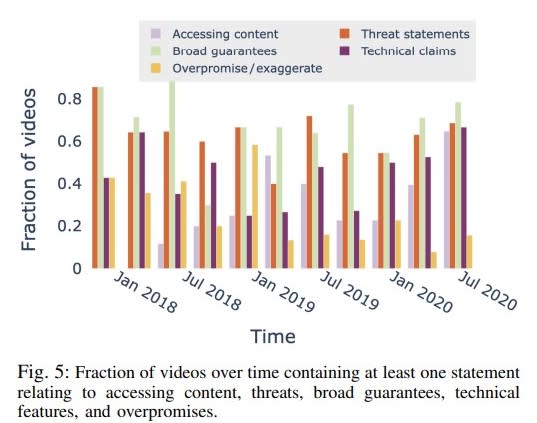
“Our analysis suggests that VPN ads make many claims that have the potential to influence viewers’ mental models not just of VPNs, but of computer security and privacy in general,” concluded the research paper after reviewing 243 YouTube videos containing these ads.
For instance, researchers found many influencers using absolute terms, false technical claims, and misleading visuals to oversell the security and privacy guarantees of the products.
Among all the providers analyzed, VirtualShield was the one with the highest ratio of videos contaminated with overpromises and exaggerations. These ads less frequently mentioned encryption and IP address routing, too, the two very features at the core of the product itself.