Cyberattack shuts down major US gas pipeline

Colonial Pipeline’s overall system is the US’ biggest, covering more than 5,500 miles and carrying more than 100 million gallons of fuel a day, the company says.
Colonial Pipeline
A cyberattack has taken down the main pipeline that carries gasoline to the US East Coast, the pipeline’s operator said Friday, further raising concern about how vulnerable critical systems are to hacking assaults.
Colonial Pipeline, which operates pipes that carry refined petroleum products like gas, diesel, jet fuel, home heating oil and fuel for the military, said in a statement that it’s taken “certain systems offline to contain the threat, which has temporarily halted all pipeline operations, and affected some of our IT systems.”
If the disruption doesn’t last beyond a few days, it likely won’t cause many problems, due to local supplies of gas that typically get replenished via the pipeline about once a week, The Wall Street Journal reported, likening the situation to pipeline shutdowns that occur during hurricanes. Still, the shutdown increases alarm about cyberattacks on key systems.
It’s unclear whether criminal hackers or a nation-state is behind the attack, the Journal reported. Colonial said it’s contacted “law enforcement and other federal agencies” and engaged a “leading, third-party cybersecurity firm” to investigate.
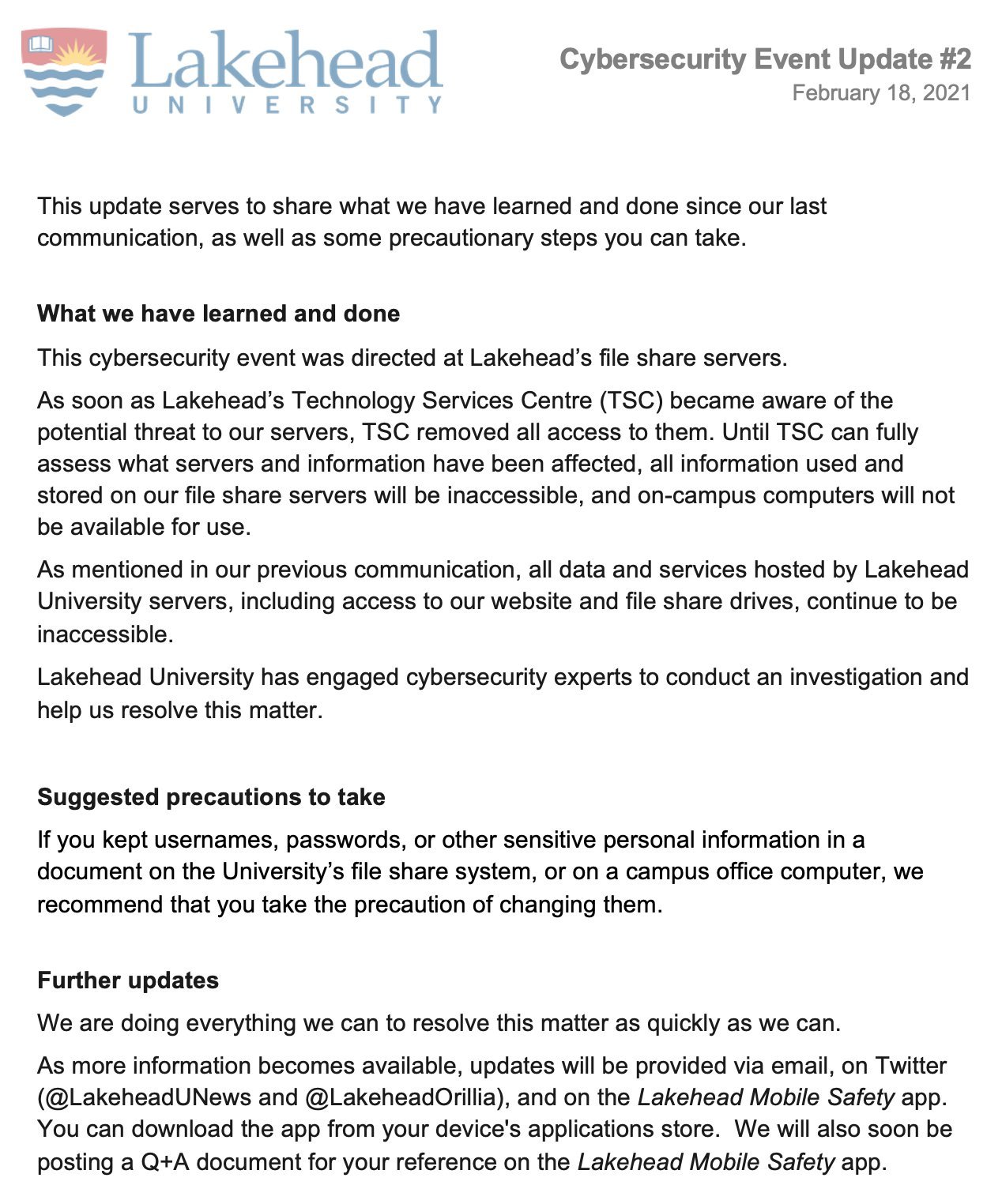
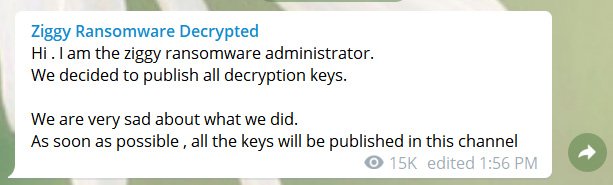
The attack involved ransomware, Colonial said in an updated statement Saturday. In such schemes, attackers use code to seize control of a computer system and then demand money to unlock it. The worldwide WannaCry ransomware attacks in 2017, for instance, locked up computer systems at hospitals, banks and phone companies.
But assaults like the one…