Report identifies phishing, ransomware attacks as most significant security incidents for healthcare

The HIMSS Healthcare Cybersecurity Survey found that across the board, healthcare organizations identified phishing and ransomware attacks as the most significant security incidents in 2021.
Financial information was the most frequent target of such cyber attacks, according to the report. Cyber threats such as ransomware attacks against the industry have grown over the years amid challenges it already confronts: aging infrastructures and tight budgets.
The report, sponsored by Carahsoft, surveyed 167 professionals to assess the state of healthcare cybersecurity. Of those surveyed, 54% worked for healthcare provider organizations, 28% for consulting/vendor organizations, and 19% for other types of organizations. Most (61%) of those surveyed had primary responsibility for cybersecurity programs at their respective healthcare organization and 23% had some responsibility. Further, of those surveyed, 90% said they had a management role in healthcare cybersecurity.
A substantial —67% — number of those who responded stated that in the past 12 months their healthcare organization combated significant security incidents, the report said. When considering how severe the security threat was that the organization faced, 12% considered it critical and 32% considered it a high threat.
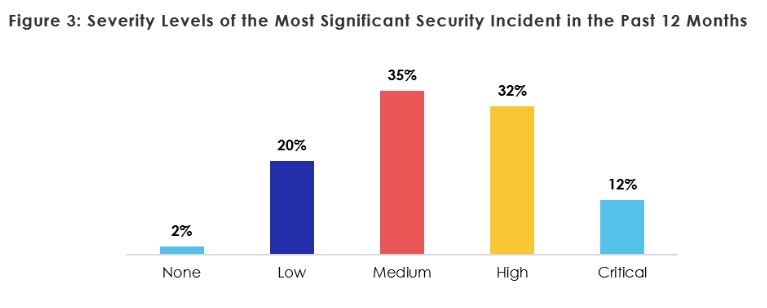
Further, healthcare organizations said phishing attack were the first most common form of threat, accounting for 45% of security incidents. Ransomware attacks ranked second, comprising 17% of incidents. 
Additionally, phishing often played a major role in the security incidents. For example, 57% of those surveyed said the most significant security incident included phishing. Respondents indicated the percentage of each type of phishing that occurred: email phishing (71%), spear-phishing (67%), voice phishing/vishing (27%), whaling (27%), business e-mail compromise (23%), SMS phishing (21%), phishing websites (20%) and social media phishing (16%), according to the report.
When exploring the initial point of contact that compromised cybersecurity, phishing was the most common, at 71%, the report said. Additionally, human error (19%) and social engineering (15%) as well as legacy software (15%) were the…



