Ransomware attacks surged 2X in 2021, SonicWall reports
Join today’s leading executives online at the Data Summit on March 9th. Register here.
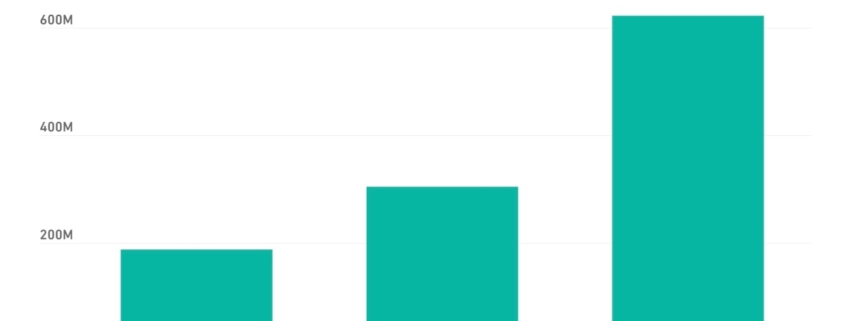
In the latest indicator of just how severe the ransomware problem became last year, new data released today by cybersecurity vendor SonicWall reveals that the total number of ransomware attacks more than doubled in 2021 – jumping 105% during the year compared to 2020.
It’s a stunning increase, considering how bad ransomware already was in 2020, and shows that ransomware has solidified its status even further as a “weapon of choice” for cyber criminals, said Bill Conner, president and CEO at SonicWall.
In case there was any doubt about it at this point, ransomware is “not going away anytime soon,” Conner said.
The data was released in the 2022 SonicWall Cyber Threat Report, and based on telemetry data from SonicWall’s customer base as well as from infrastructure such as honeypots operated by the company’s threat research team. SonicWall offers security products across network, email, endpoint, and secure access, and reports having more than 500,000 customers.
Due to the massive amount of data that SonicWall is able to capture, the company says that its findings can be viewed as representative of the ransomware issue on the whole. The findings are a “statistical proxy for what’s going on out there” in terms of overall ransomware attacks, said Dmitriy Ayrapetov, vice president of platform architecture at SonicWall.
Accelerated threat
The 105% spike in ransomware attacks in 2021 was also a significant acceleration from the rate of increase in the previous year, when ransomware attacks climbed 62%, year-over-year, according to SonicWall.
And compared to 2019, ransomware attacks were more than three times higher in 2021, marking a 231% increase in two years, the report says.
To put the 2021 ransomware surge further in perspective, the worst month for attacks in 2020 would’ve qualified as one of the better months in 2021, according to the report.
The bottom line is that ransomware is only growing in popularity with cyber criminals because it’s “where the money is,” Ayrapetov said. “If you’re going to monetize an attack, and want…


 Print
Print

