Anti Ransomware Market Challenges 2023: Size, Share, and Forecasts | Sophos, Check Point, Cybereason
Step into the world of boundless opportunities in the global Anti Ransomware market with INFINITY BUSINESS INSIGHTS as your trusted partner. Our report goes beyond mere information; it’s your gateway to unlocking unparalleled potential. Dive deep into the market’s intricacies, exploring End User insights, Types, Applications, Major Players, and more. With our global forecast spanning from 2023 to 2030, you’ll gain the power to anticipate trends and seize the future. Be the industry leader, armed with the knowledge to outperform the competition. Join us in this exciting adventure, where data shapes destiny, and innovation leads to success. The global Anti Ransomware market beckons, and we hold the key to unlock its untapped potential.
Market Expansion Forecast:
Foresee a robust Compound Annual Growth Rate (CAGR) of 17.6% in the Anti Ransomware market from 2023 to 2030.
Click to get Anti Ransomware Market Research Sample PDF Copy Here @
https://www.infinitybusinessinsights.com/request_sample.php?id=1691835&MODE=hpp
The Key Players in this Market are:
Sophos, Check Point, Cybereason, Faronics, Bitdefender, Malwarebytes, Kaspersky, Mimecast, Seqrite, Trend Micro, Clonix, McAfee, Acronis, Qihoo 360
The Anti Ransomware Market encompasses software solutions and services designed to detect, prevent, and mitigate ransomware attacks. Ransomware is a type of malware that encrypts a victim’s data and demands a ransom for its decryption. Anti-ransomware tools help organizations protect their data and systems by identifying and blocking ransomware threats, providing backup and recovery options, and strengthening cybersecurity measures. This market serves businesses and individuals across various sectors who aim to safeguard their digital assets and sensitive information from ransomware attacks, which continue to pose a significant cybersecurity threat. As ransomware attacks evolve, the Anti Ransomware Market continues to evolve with innovative security solutions.
Secure Your Insights: Purchase the Full Report Now:
https://www.infinitybusinessinsights.com/checkout?id=1691835&price=&MODE=hpp
Global Anti Ransomware: Scope of the Report:
Our comprehensive market analysis delves into the Global Anti…

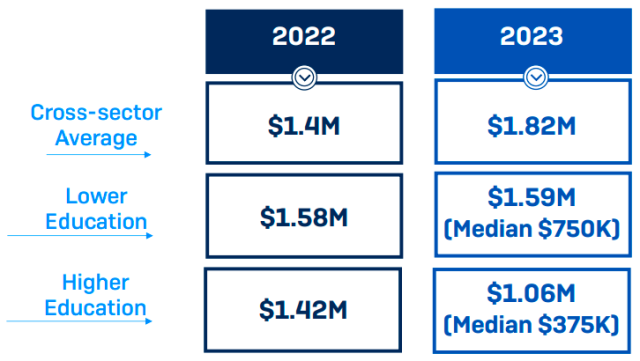
 The ability to recover encrypted data is crucial for organizations facing ransomware attacks. Fortunately, all higher education institutions and 99 percent of lower education organizations were successful in recovering their data. Notably, the recovery rate for the education sector surpasses the cross-sector average, indicating a degree of resilience in the face of such threats.
The ability to recover encrypted data is crucial for organizations facing ransomware attacks. Fortunately, all higher education institutions and 99 percent of lower education organizations were successful in recovering their data. Notably, the recovery rate for the education sector surpasses the cross-sector average, indicating a degree of resilience in the face of such threats.

