SharkBot Malware Reappears in the Google Play Store

The best way to prevent malware from creeping onto your Android phone is to only download apps from the official Play Store. However, no method is foolproof. Malware creators occasionally find a way to hide malware in Google’s repository, at least for a little bit. Earlier his year, security researchers spotted a malicious software package called SharkBot spreading through the Play Store. It was stamped out, of course, but now it’s back with a vengeance.
In the early days of the Play Store, Google would allow every app to go live with minimal oversight. Slowly, it has ratcheted up its automated and human-powered checks, which makes it very difficult to upload a known piece of malware. So, most malware campaigns today attempt to distribute a seemingly innocuous app that then downloads a malicious payload. That’s what SharkBot does.
When originally detected in February 2022, SharkBot dropper was ironically pretending to be an antivirus app. It used Android’s Accessibility service to download and install its malicious code without user interaction, giving the creators access to banking information, keystrokes, and even the ability to take over a phone completely. The latest version even adds a feature to steal login cookies so the attackers can access user accounts.
The new dropper doesn’t have the same installation trick. Google has started cracking down on apps that use the Accessibility service for exactly this reason. The same systems that help disabled people use their phones can be hijacked to install malware without the user’s knowledge. Now, apps that call for Accessibility need to have a good reason, and Google will boot apps that don’t. Instead, the new SharkBot dropper downloads the malware, which masquerades as a fake security update and has to be installed by the user.
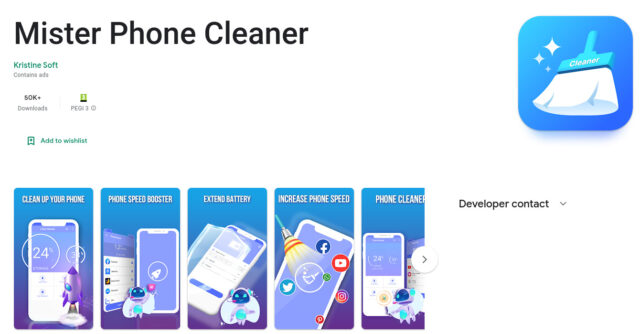
One of the listings for the new SharkBot dropper.
Since the new dropper can’t use Accessibility to get the job done, it relies on the user to manually allow unknown sources and install the dangerous code. That’s much less likely, but it still happens. The dropper popped up in several listings,…