Mirai-based NoaBot Botnet Targeting Linux Systems with Cryptominer
A noticeable difference between NoaBot and Mirai is that rather than DDoS attacks, the botnet targets weak passwords connecting SSH connections to install cryptocurrency mining software.
Cybersecurity researchers at Akamai have discovered cryptomining malware called NoaBot based on the notorious Mirai botnet. The crytojacking malware NoaBot is currently targeting Linux servers and has been active since January 2023.
According to Akamai, a noticeable difference between NoaBot and Mirai is that rather than DDoS attacks (Distributed Denial of Service attacks), the malware targets weak passwords connecting SSH connections and installs cryptocurrency mining software, allowing attackers to generate digital coins using victims’ computing resources, electricity, and bandwidth.
Here, it is important to mention that NoaBot malware has also been used to deliver P2PInfect, a separate worm discovered by Palo Alto Networks in July 2023.
NoaBot is compiled using the UClibc code library, unlike the standard Mirai library. This changes how the antivirus protections detect NoaBot, categorizing it as an SSH scanner or generic trojan. The malware is statically compiled and stripped of symbols, while strings are obfuscated instead of saved as plaintext, making it harder for reverse engineers to extract details.
The NoaBot binary runs from a randomly generated folder, making searching devices harder. The standard Mirai dictionary is replaced with a large one, and a custom-made SSH scanner is used. Post-breach capabilities include installing a new SSH-authorized key.
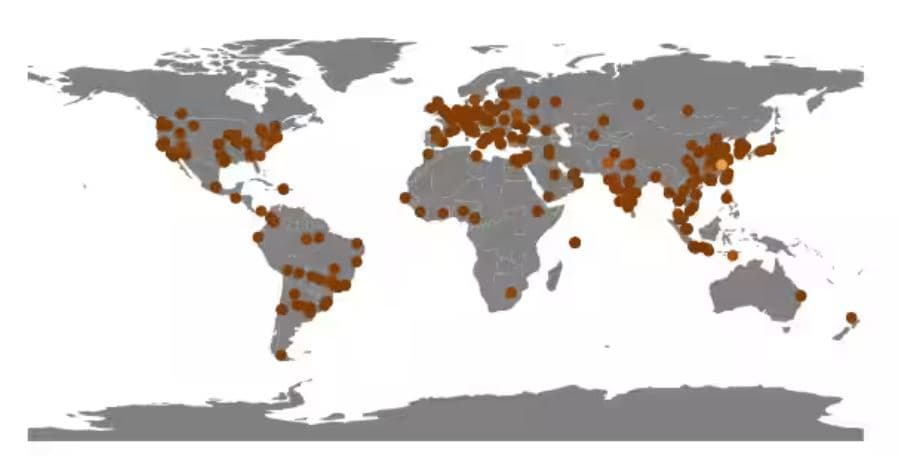
This botnet has grown significantly, with over 800 unique IP addresses worldwide showing signs of NoaBot infections. The worm is a customized version of Mirai, a malware that infects Linux-based servers, routers, web cameras, and other Internet of Things devices.
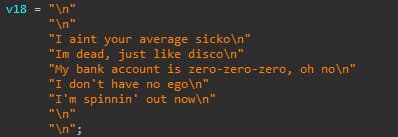
Interestingly, the malware includes embedded song lyrics from the “Who’s Ready for Tomorrow” song by Rat Boy and IBDY, but later samples do not have these. The botnet also adds command line arguments, such as the “noa” flag, which installs a persistence method after a reboot.
Threat actors…