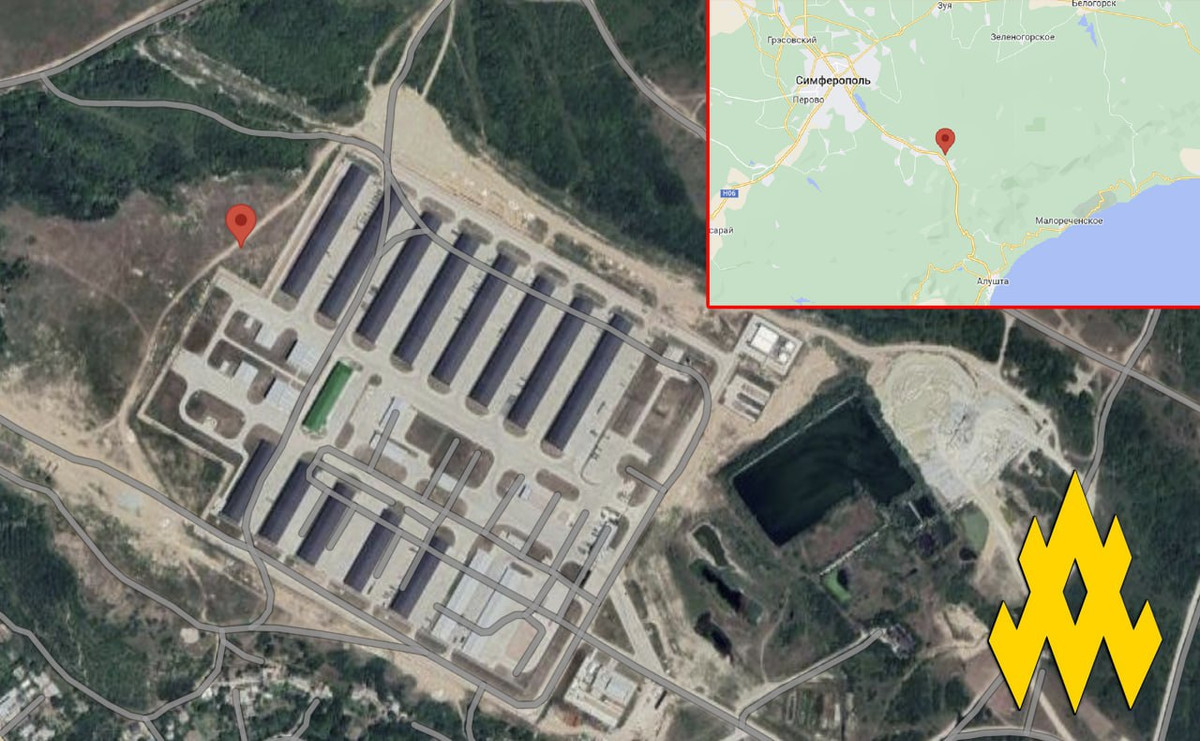
Ukraine Tracks a Record Number of Cyber Incidents During War
Cyberwarfare / Nation-State Attacks
,
Fraud Management & Cybercrime
Hackers Steal CCTV Footage to Study Efficacy of Missile Strikes and Drone Attacks

The tempo of cyberattacks against Ukrainian critical infrastructure has intensified this year – the second year in which Kyiv is fending off a Russian war of conquest.
See Also: OnDemand | Ransomware in the Cloud: Challenges and Security Best Practices
In the first 10 month of this year, Ukraine’s national computer emergency response team, CERT-UA, logged 2,054 cyber incidents, compared to 2,194 for the entirety of 2022, said Viktor Zhora, deputy chairman of Ukraine’s State Service of Special Communications and Information Protection. Three-quarters of the incidents involved civilian infrastructure, Zhora told a cybersecurity conference in Dublin on Thursday.
Hackers’ top goals are to steal information on the disposition of forces, infiltrate organizations that provide critical infrastructure services and steal people’s personal information from organizations across a number of sectors, including insurance and healthcare, said Zhora, who addressed the IRISSCON conference, held by IRISSCERT – short for the Irish Reporting and Information Security Service – via video link.
Since Russia launched an all-out invasion on Feb. 24, 2022, the most dangerous hacking incidents have typically traced to Russia’s GRU military intelligence group, he said. The greatest number of attacks this year appear to have been launched by the Federal Security…