Tag Archive for: vector
VMware Flaw a Vector in SolarWinds Breach? — Krebs on Security
/in Computer Security
U.S. government cybersecurity agencies warned this week that the attackers behind the widespread hacking spree stemming from the compromise at network software firm SolarWinds used weaknesses in other, non-SolarWinds products to attack high-value targets. According to sources, among those was a flaw in software virtualization platform VMware, which the U.S. National Security Agency (NSA) warned on Dec. 7 was being used by Russian hackers to impersonate authorized users on victim networks.
On Dec. 7, 2020, the NSA said “Russian state-sponsored malicious cyber actors are exploiting a vulnerability in VMware Access and VMware Identity Manager products, allowing the actors access to protected data and abusing federated authentication.”
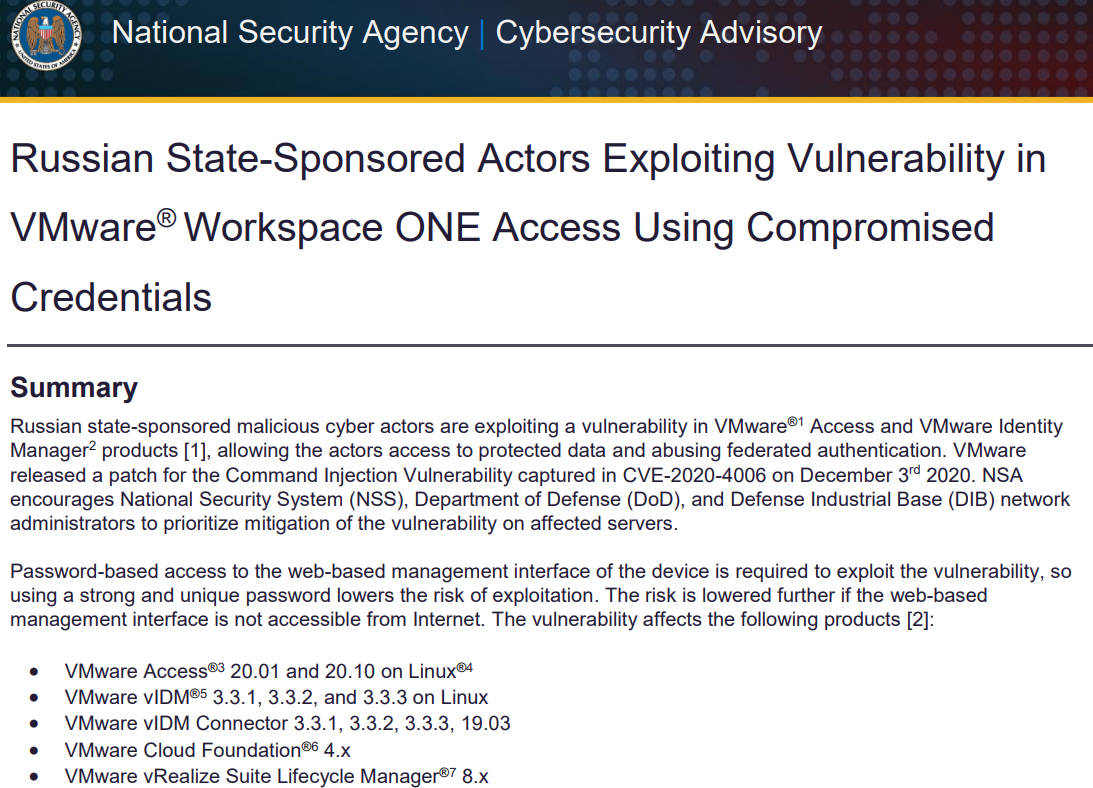
VMware released a software update to plug the security hole (CVE-2020-4006) on Dec. 3, and said it learned about the flaw from the NSA.
The NSA advisory (PDF) came less than 24 hours before cyber incident response firm FireEye said it discovered attackers had broken into its networks and stolen more than 300 proprietary software tools the company developed to help customers secure their networks.
On Dec. 13, FireEye disclosed that the incident was the result of the SolarWinds compromise, which involved malicious code being surreptitiously inserted into updates shipped by SolarWinds for users of its Orion network management software as far back as March 2020.
In its advisory on the VMware vulnerability, the NSA urged patching it “as soon as possible,” specifically encouraging the National Security System, Department of Defense, and defense contractors to make doing so a high priority.
The NSA said that in order to exploit this particular flaw, hackers would already need to have access to a vulnerable VMware device’s management interface — i.e., they would need to be on the target’s internal network (provided the vulnerable VMware interface was not accessible from the Internet). However, the SolarWinds compromise would have provided that internal access nicely.
In response to questions from KrebsOnSecurity, VMware said it has “received no notification or indication that the CVE 2020-4006 was used in conjunction with the…
‘Compromised credentials’ most likely vector in Trump re-election site defacement
/in Internet Security
Make Websites Safe Again

Donald Trump’s official re-election campaign website was briefly defaced on Tuesday (October 27) in an embarrassing rather than serious lapse of security.
As-yet-unknown attackers left a message on donaldjtrump.com claiming they had compromising information on the US president, suggesting a conspiracy theory that “trump-gov is involved in the origin of the coronavirus” as well as supposedly being in cahoots with “foreign actors manipulating the 2020 elections”.
Visitors to the site were encouraged to vote on whether or not this supposed compromising material would be released by sending funds to one of two Monero cryptocurrency wallet IDs, each publicised through the defacement.
Which wallet received the most money would ostensibly determine the outcome of the vote.
Of course, the highly visible defacement on such a high-profile website didn’t stay up for long, so the exercise failed to rake in significant funds.
Gone in a flash
The defacement message – which parodied notices typically posted when the FBI seizes control of web services operated by cybercriminals – was pulled within minutes and the site quickly restored with approved content, encouragements to make campaign donations, or buy Republican Party merchandise.
A post on Twitter by the Trump re-election campaign’s director of communications, Tim Murtaugh, stated that “there was no exposure of sensitive data” because none is stored on the site.
Catch up on the latest election security news
The Trump campaign was “working with law enforcement authorities to investigate the source of the attack”, he added.
Donald Trump’s campaign website is hosted using ExpressionEngine, a content management system, and served through Cloudflare’s content delivery network.
 Donald Trump’s re-election campaign website was briefly defaced on October 27
Donald Trump’s re-election campaign website was briefly defaced on October 27
Wordfence analysis
In the wake of the short-lived attack, researchers from web security firm Wordfence offered some analysis of how the hack might have been carried out.
Since the…



