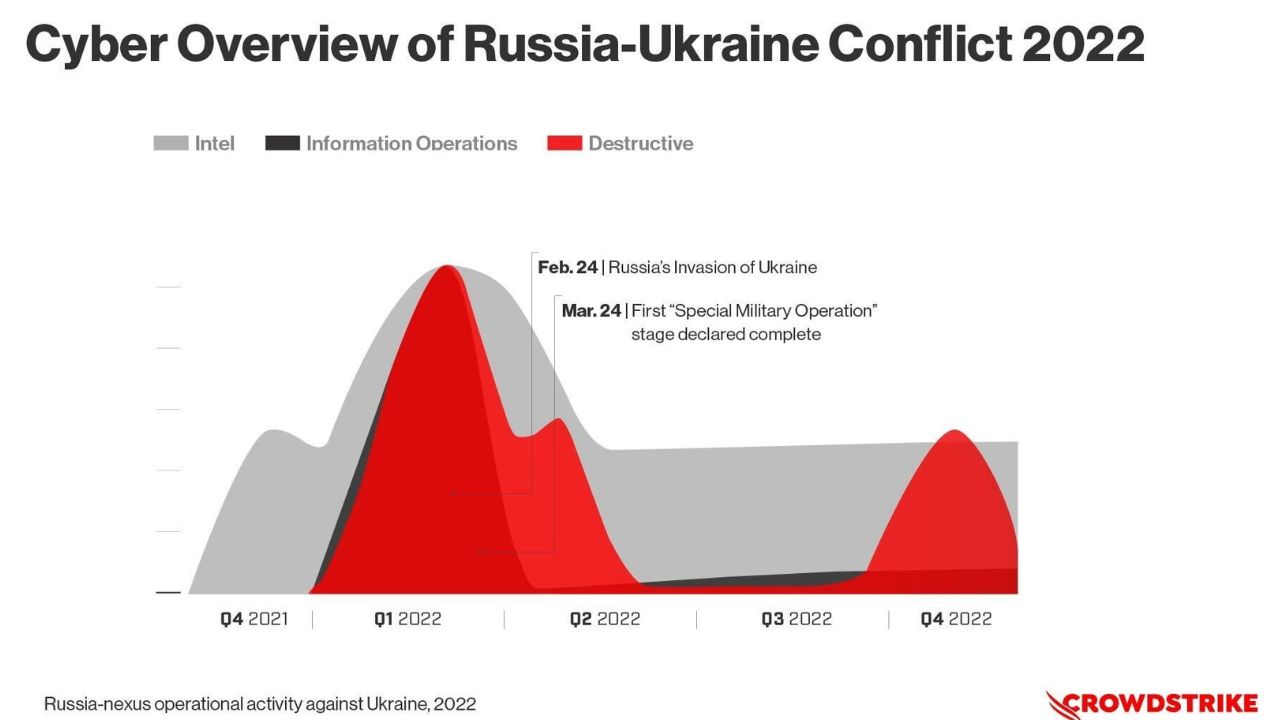
A year of wipers: How the Kremlin-backed Sandworm has attacked Ukraine during the war
Last November, several Ukrainian organizations were targeted by a new type of ransomware called RansomBoggs. Its operators sent infected computers a ransom note written on behalf of James P. Sullivan — the main protagonist of the animated film Monsters, Inc.
In the note Sullivan, whose job in the movie was to scare kids, asked for financial help in exchange for decrypting the organizations’ documents.
The hackers behind the attack are believed to be linked to Sandworm, a Russian nation-state threat actor working on behalf of the military intelligence agency GRU. But despite the attack wearing all the trappings of ransomware, Sandworm wasn’t out to make money — its primary goal was either to destroy Ukrainian networks or steal valuable data, according to researchers from the Slovak cybersecurity company ESET, which first spotted the RansomBoggs attack.
While Sandworm is not the Kremlin’s most important hacking group, it has perhaps become the most visible one, with an emphasis on disruptive cyberattacks. And its track record of successful attacks with a global impact – most notably the NotPetya malware and several attacks on Ukraine’s power supply – make it a grave concern to researchers.
In 2017, the group used NotPetya wiper malware disguised as ransomware to take down hundreds of networks across Ukrainian government agencies, banks, hospitals, and airports, causing an estimated $10 billion in global damage. By presenting destructive attacks as ransomware, Sandworm hackers may be trying to cover their tracks and make it more difficult for security researchers to attribute the attacks to a state-sponsored group.
In the case of the RansomBoggs attacks, the group was likely testing new techniques or training new workers on how to use their software, ESET senior malware researcher Anton Cherepanov told The Record.
Since the start of the war, Sandworm has been relentlessly targeting Ukraine with various malware strains. Some were highly sophisticated, while others contained bugs that made them easier to detect and prevent from spreading.
Researchers believe that Sandworm chose to experiment with malware in order to find strains that can bypass Ukraine’s improved…