Watch out for this new malicious ransomware disguised as Windows updates
Is that really a Windows update you are about to click on? Or ransomware in disguise? As first documented by Fortinet FortiGuard Labs and followed up by Trend Micro, new ransomware is currently on the rise and disguising itself as fake Windows updates and Word installers as part of a malvertising campaign. Also, multiple variants of this ransomware have been discovered.
Here’s what we know so far and what you can do to protect yourself.
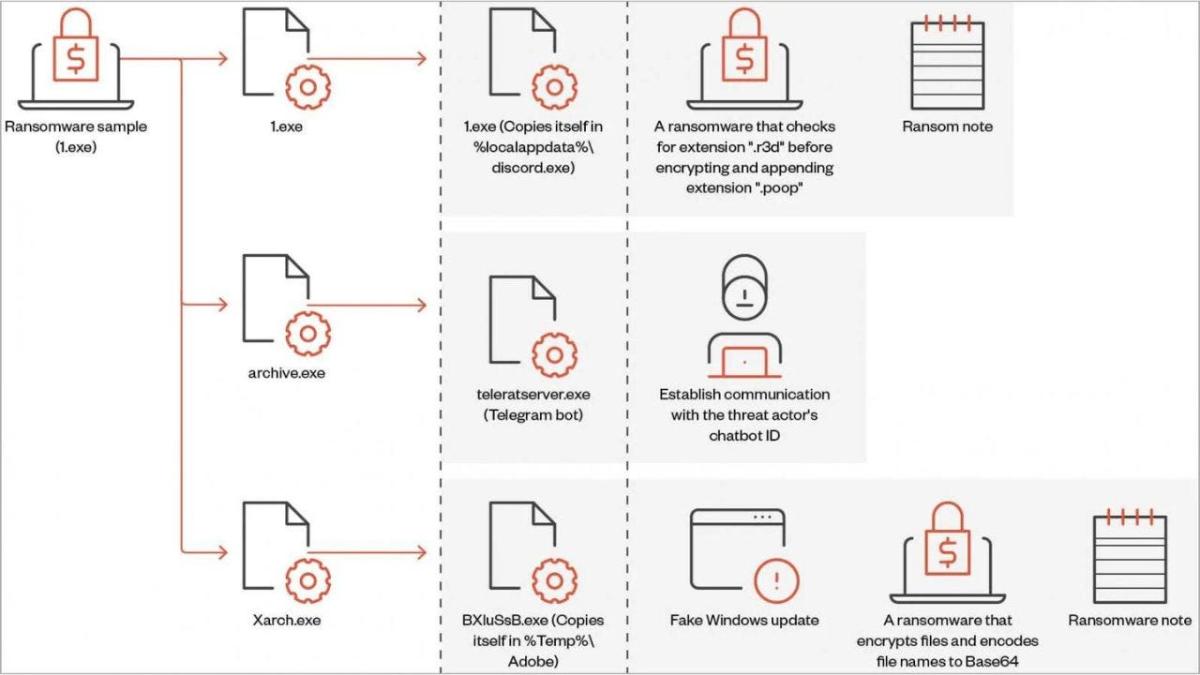
The ransomware, which is called Big Head, infects devices and encrypts the device’s files by displaying a fake Windows update alert on the victim’s computer. Three encrypted executable files are deployed in the attack – one for propagating the malware, one for facilitating communications via Telegram, and one for encrypting the files and displaying the fake Windows update.
If a person clicks on this fake Windows update alert, Big Head will begin its attack by deleting backups, checking the virtualized environment, disabling the computer’s Task Manager to prevent the user from deleting it, and more.
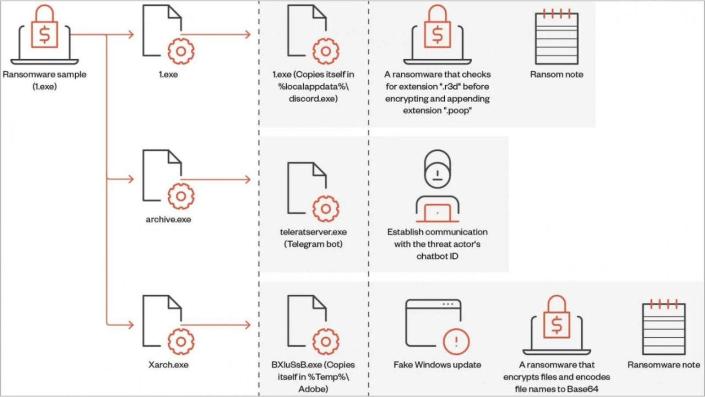
There have also been variants discovered of the Big Head ransomware that are capable of stealing web browser history, directory lists, running processes, product keys and network information. Most of the samples of this ransomware have been submitted from the U.S., France, Turkey and Spain.
RUSSIAN RANSOMWARE ATTACK SOFTWARE TARGETS APPLE MAC AND MACBOOK
Ransomware criminals will try to get you to pay money to them to get your files back. However, paying the ransom does not guarantee that you will regain access to anything a criminal takes from you and will only permit them to do it more.
Your best bet is to prevent an attacker from gaining access to your files altogether so that you don’t have to try to fight to get them back. Here are some of my tips for avoiding having your files stolen in a ransomware attack.
If you receive an…