Portugal investigates dark web sale of classified NATO documents – EURACTIV.com
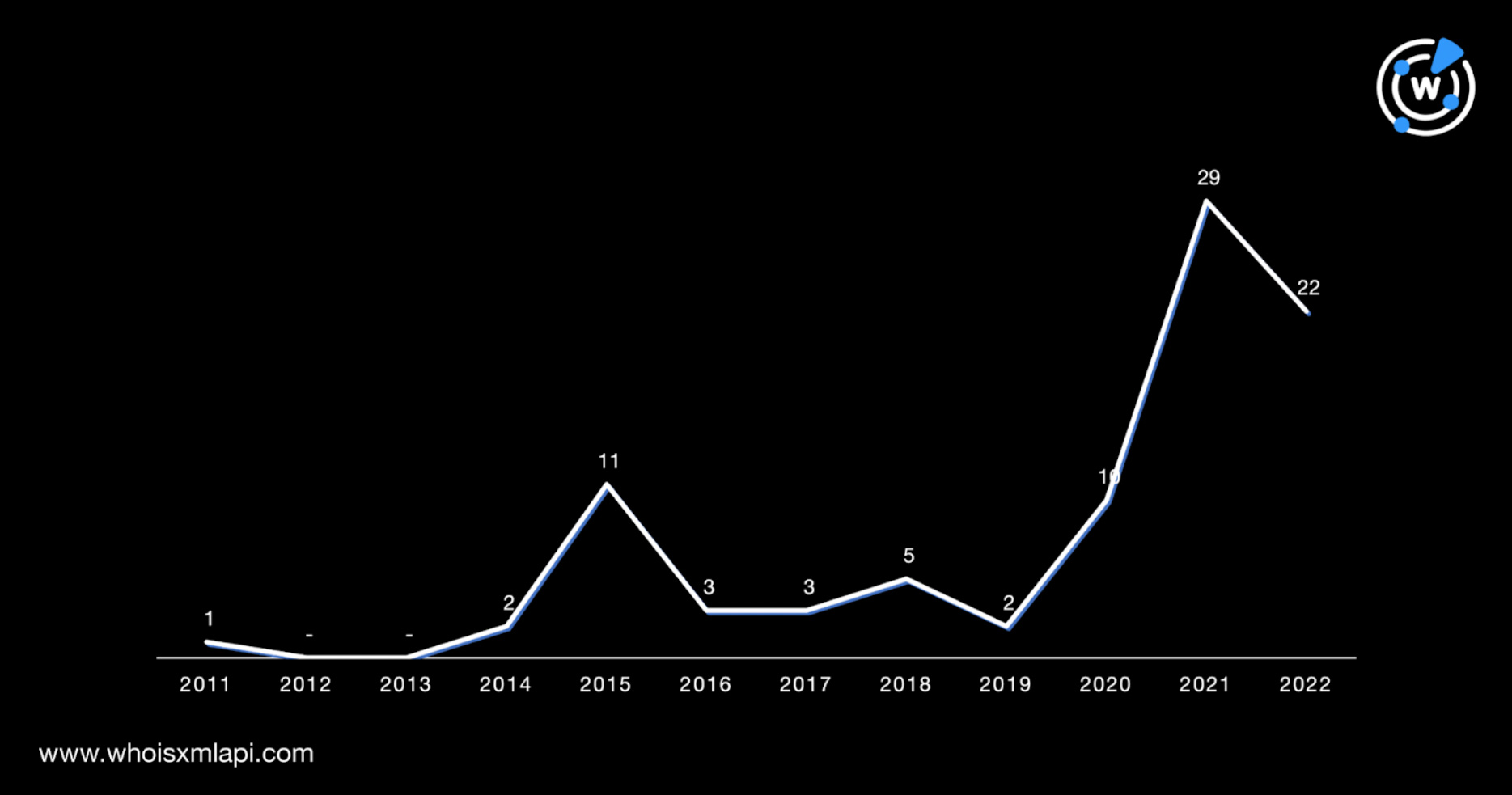
Portugal’s public prosecutor’s office is investigating a cyberattack against the Armed Forces General Staff in which classified NATO documents were extracted and put up for sale on the ‘dark web’, the Attorney General’s Office said on Tuesday.
“The establishment of an enquiry is confirmed. It is led by the public prosecutor’s office of the Central Department of Investigation and Prosecution (DCIAP),” the Attorney General’s Office told EURACTIV’s media partner Lusa.
According to the Portuguese newspaper Diário de Notícias, the government was informed of the situation last week by the US intelligence services, via the embassy in Lisbon, through a communication that was reportedly made directly to Prime Minister António Costa in August.
The same newspaper mentioned that this case was considered “extremely serious” and that US cyber spies had detected “for sale on the ‘dark web’ hundreds of documents sent by NATO to Portugal, classified as secret and confidential.”
The Defence Ministry said it was already investigating “all signs of a potential breach of computer security” and claimed the “sensitivity” of the proceedings meant further comment was not appropriate.
In a statement, the ministry said that the investigations are conducted by the National Security Office, “with which the ministry of defence and the armed forces work in close coordination.”
Among the functions of the National Security Office is to “ensure the security of classified information within the national framework and international organisations to which Portugal is a party” and exercise “the function of accreditation authority for natural or legal persons to access and handle classified information.
(Fernando Carneiro/Lusa.pt)