What’s new and improved in Windows 11 22H2, coming soon

Windows 11 version 22H2 aka Sun Valley 2 is set to launch later this year. Unlike the original Windows 11 release, it won’t be a massive update with radical design changes.
Instead, Sun Valley 2 will be similar to Windows 10 Anniversary Update, so you can expect minor improvements and a few new features.
The version 22H2 will contain a number of improvements and it will be offered as a full feature update rather than an enablement package.
Start Menu improvements
Microsoft is testing a new feature that will allow you to pin more apps or activities in the recommendations section of the Start Menu.
Additionally, you can soon force the Start Menu recommendations tab to open files in Office web only if your device doesn’t come with full desktop apps.
There’s a possibility that Start Menu features will be released using ‘Windows Feature Experience Packs,’ which is a new way to update and improve the OS without major feature updates.
Taskbar
Microsoft is restoring the drag and drop capability. This means you can finally drag your files onto apps pinned to the taskbar. Or you can also drag apps to the taskbar to create shortcuts.
Task Manager
22H2 will refresh Task Manager with a new design based on Fluent UI and WinUI.
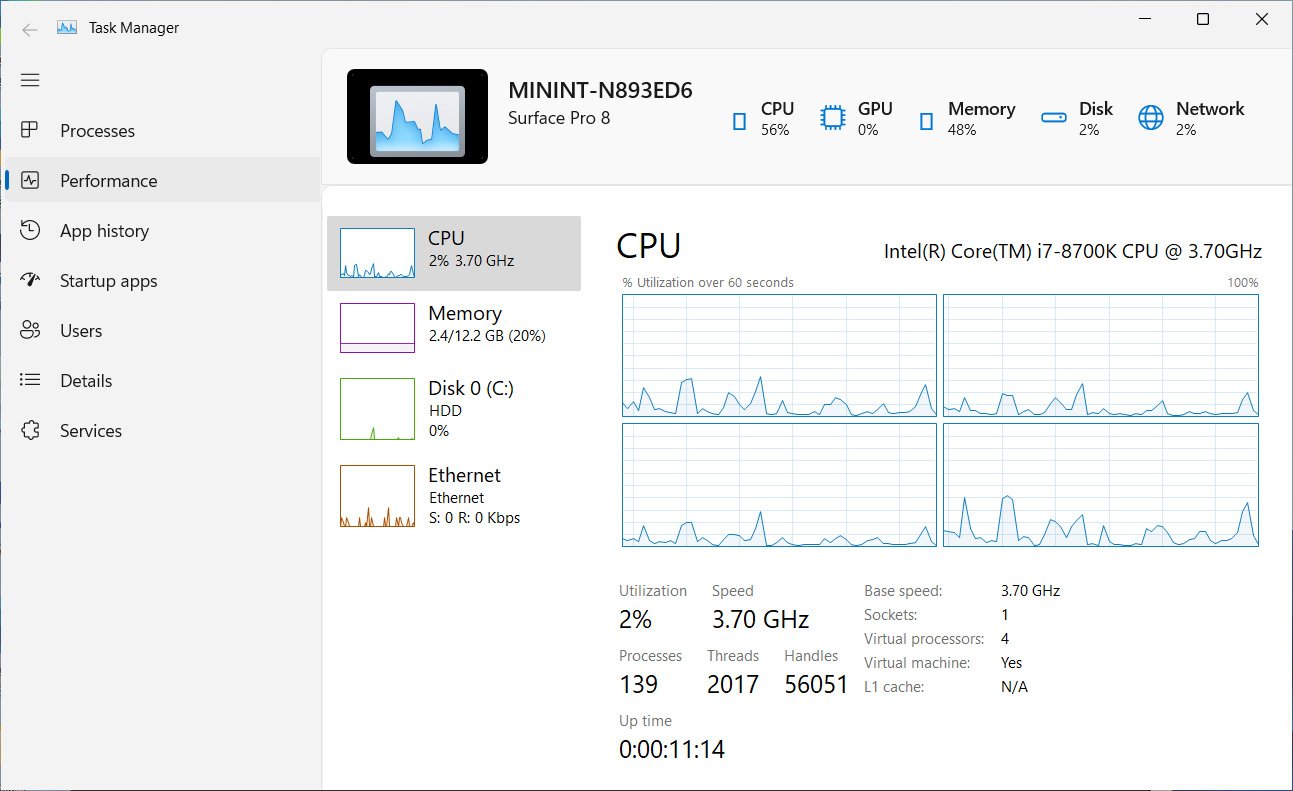
Like the current version of Task Manager, the new version can also display the same set of screens, such as Processes, Performance, App history, Startup apps, Users, Details, and services. However, there are a few noticeable changes.
As you can see in the below screenshots, Task Manager will now use a new sidebar or hamburger menu to display processes and performance options. This would make the Task Manager easily accessible on touchscreen devices.
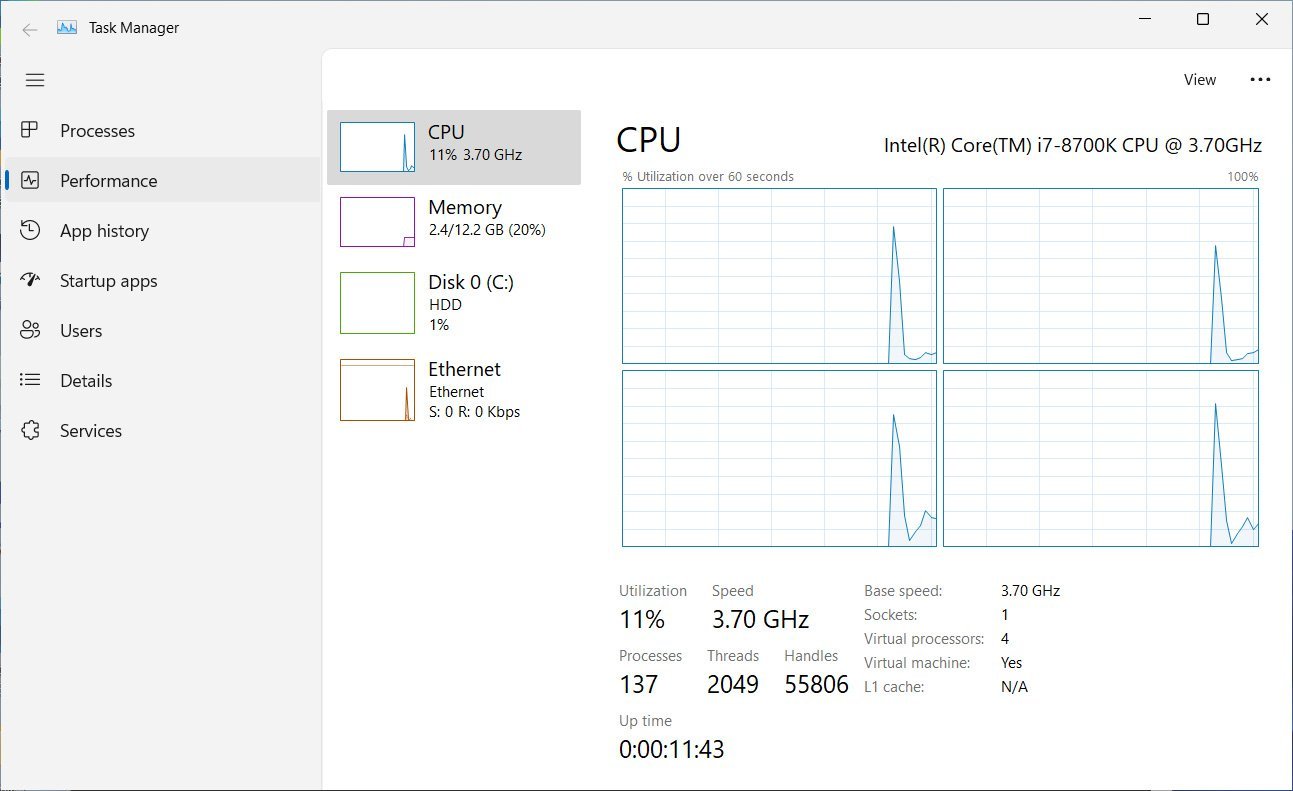
Additionally, Task Manager’s top bar now displays the brand and name of the device, its model (if available), a picture of the device, and CPU or RAM being used.
New flyout design
Microsoft is refreshing the design for the hardware indicators like sound and brightness.
Media controls that appear on the Lock screen when playing music in a supported app are also getting a new look.

The updated flyout matches the design shown for the media controls across the operating system and Microsoft’s vision for…



