Week in review: Account pre-hijacking, Sigstore, ransomware still winning

Here’s an overview of some of last week’s most interesting news, articles, interviews and videos:
RansomHouse: Bug bounty hunters gone rogue?
A new cybercrime outfit that calls itself RansomHouse is attempting to carve out a niche of the cyber extortion market for itself by hitting organizations, stealing their data, and offering to delete it and provide a full report on how and what vulnerabilities were exploited in the process – all for a fee, of course.
Account pre-hijacking attacks possible on many online services
Online accounts getting hijacked and misused is an everyday occurrence, but did you know that account pre-hijacking attacks are also possible?
Verizon 2022 DBIR: External attacks and ransomware reign
There has been an alarming rise (13%) in ransomware breaches – a jump greater than the past 5 years combined, Verizon Business has revealed in its 2022 Data Breach Investigations Report (2022 DBIR).
GM, Zola customer accounts compromised through credential stuffing
Customers of automaker General Motors (GM) and wedding planning company Zola have had customer accounts compromised through credential stuffing, and the criminals have used the access to redeem gift cards.
3 key elements to protect a Kubernetes cluster
Kubernetes changed how we structure, deploy, and run our applications and became a de-facto standard for running infrastructure at scale. With the rapid adoption of container-based technologies, organizations are increasingly concerned about the security of their Kubernetes clusters.
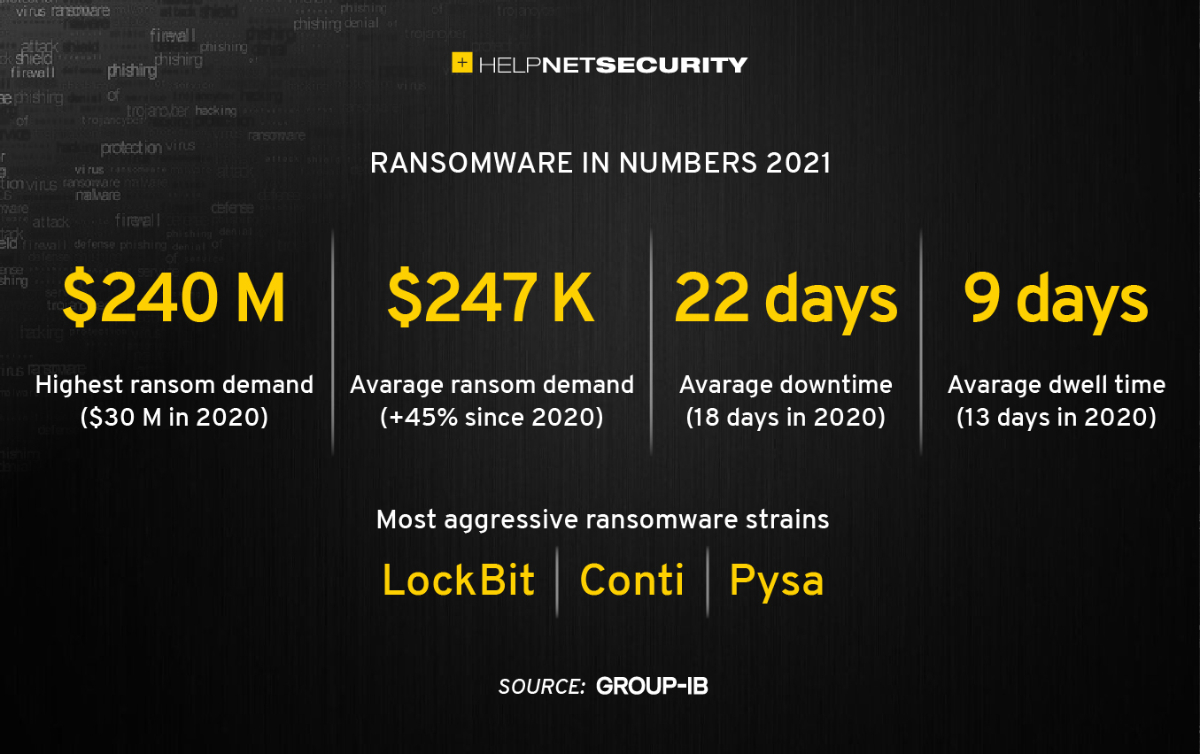
Ransomware still winning: Average ransom demand jumped by 45%
Group-IB unveils its guide to the evolution of threat number one “Ransomware Uncovered 2021/2022”.
What does prioritizing cybersecurity at the leadership level entail?
Week after week, month after month, shareholder cyber lawsuits hit the news. Capital One settles for $190 million. A class-action lawsuit was filed against Ultimate Kronos Group for alleged negligence regarding a ransomware attack, identifying a poor cybersecurity system as the root problem.
Elevation of Privilege is the #1 Microsoft vulnerability category
BeyondTrust announced the release of a report which includes the latest annual…