Week in review: MS Exchange zero-days exploited, AD attack paths, developing secure APIs

SpyCast: Cross-platform mDNS enumeration tool
SpyCast is a cross-platform mDNS enumeration tool that can work either in active mode by recursively querying services or in passive mode by only listening to multicast packets.
Attackers use novel technique, malware to compromise hypervisors and virtual machines
Unknown attackers wielding novel specialized malware have managed to compromise VMware ESXi hypervisors and guest Linux and Windows virtual machines, Mandiant threat analysts have discovered.
To encrypt or to destroy? Ransomware affiliates plan to try the latter
Researchers from Symantec, Cyderes and Stairwell have recently analyzed a new version of the Exmatter data exfiltration tool and have spotted a new capability: data corruption.
MS SQL servers are getting hacked to deliver ransomware to orgs
Cybercriminals wielding the FARGO (aka Mallox, aka TargetCompany) ransomware are targeting Microsoft SQL (MS SQL) servers, AhnLab’s ASEC analysis team has warned.
3 ways to gauge your company’s preparedness to recover from data loss
Where you store your data backup is nearly as important as creating copies in the first place. Storing your data in the cloud does not mean it is secure.
Two Microsoft Exchange zero-days exploited by attackers (CVE-2022-41040, CVE-2022-41082)
Attackers are leveraging two zero-day vulnerabilities (CVE-2022-41040, CVE-2022-41082) to breach Microsoft Exchange servers.
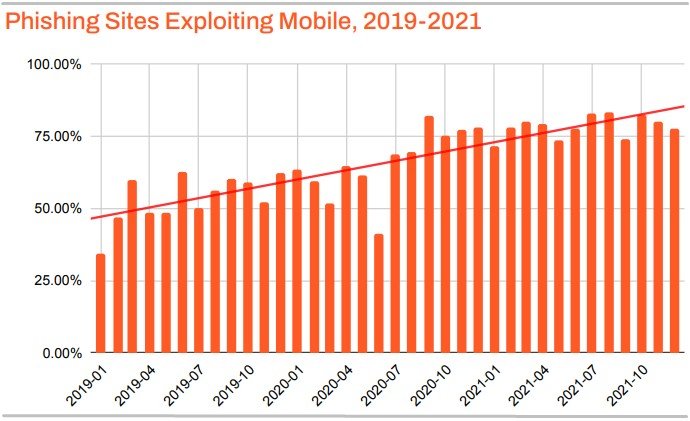
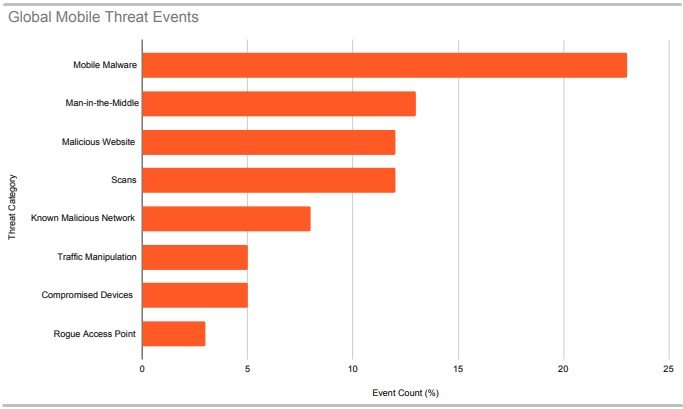
Phishing attacks skyrocketing, over 1 million observed
The APWG’s Phishing Activity Trends Report reveals that in the second quarter of 2022, the APWG observed 1,097,811 total phishing attacks — the worst quarter for phishing that APWG has ever observed.
RCE in Sophos Firewall is being exploited in the wild (CVE-2022-3236)
Sophos has patched an actively exploited remote code execution vulnerability (CVE-2022-3236) in its Firewall solutions, and has pushed the fix to customers who have automatic installation of hotfixes enabled.
The various ways ransomware impacts your organization
Despite increased investment in tools to fight ransomware, 90% of organizations were affected by ransomware in some capacity over the past 12 months, according to SpyCloud’s 2022 Ransomware Defense…