Hackers Exploit Community Meetings to Spread Malware Via Fake Zoom Invites
Hackers have been spoofing invite reminders for virtual meetings at community associations and school boards in a bid to infect attendees with malware.
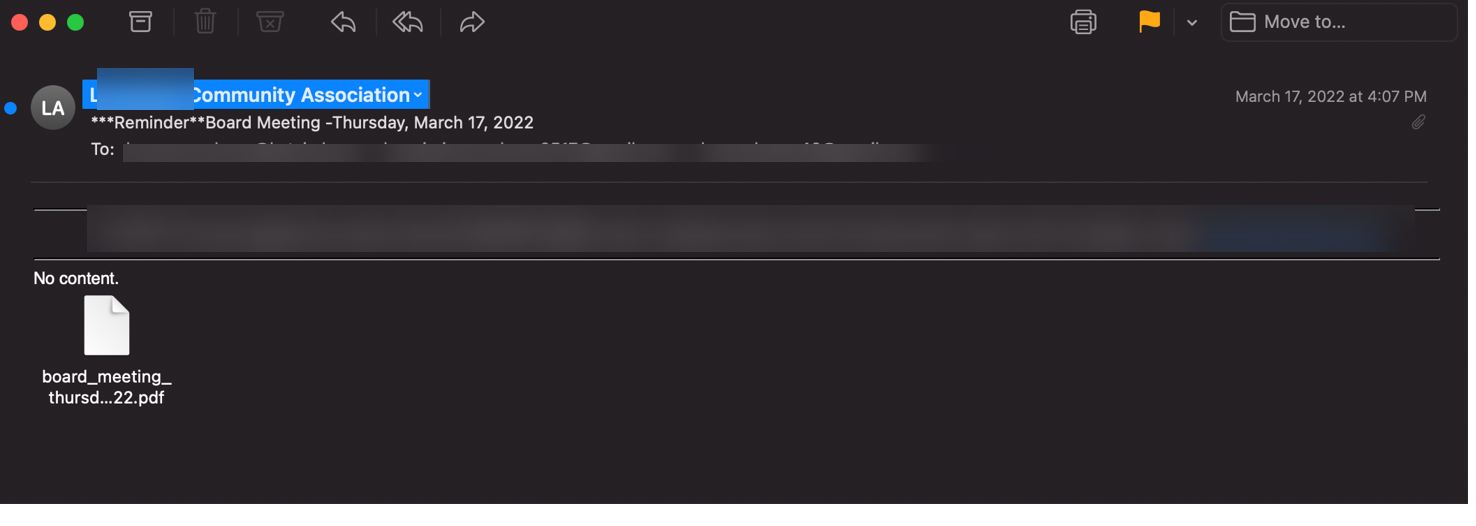
Email protection provider Avanan noticed(Opens in a new window) the attacks in March. Hackers send out emails that pretend to come from a community group or school board, but the included PDF has been designed to infect a recipient’s PC with malware.
The scheme leverages how the COVID-19 pandemic caused many people and community groups to adopt video calls as a way to meet online. Now it’s become common for users to encounter invites and reminders for virtual meetings in their email inboxes.
Unfortunately, hackers know they can exploit the same meetings to spread malware and instigate other nefarious schemes, such as “Zoom bombing.” In this case, Avanan noted the attackers will pretend to send fake meeting invites for the Zoom video-conferencing software.
(Avanan)
“It is easy for this attack to show legitimacy,” the security firm wrote in a blog post. “The association spoofed is legitimate; all public meetings are public records, so the dates can match. With just a PDF, it can easily look like a calendar invite attached to an email.”
When clicked, the PDF-based invite can then forward a user to a website that’ll ask them to download a malicious program to their machine. “The code embeds itself into system memory and can share contents of the local computer with the malicious party,” Avanan added.
Recommended by Our Editors
Avanan also warns the hackers could easily expand their attacks to target more victims. “There are countless community associations across the country and world. There are also tons of video conferencing platforms to leverage,” the security firm said.
To avoid getting phished, you should always check the sender address before interacting with an email. If something looks off, the email is most likely spoofed. Another red flag is if the email asks you to download software from an unofficial website. When in doubt, ask the administrator of a community association or school board if they in fact sent out the email in question.
Like What You’re Reading?
Sign up for SecurityWatch…





