Zyxel warns of flaws impacting firewalls, APs, and controllers

Zyxel has published a security advisory to warn admins about multiple vulnerabilities affecting a wide range of firewall, AP, and AP controller products.
While the vulnerabilities aren’t rated as critical, they are still significant on their own and can be abused by threat actors as part of exploit chains.
Large organizations use Zyxel products, and any exploitable flaws in them immediately capture the attention of threat actors.
The four flaws disclosed in Zyxel’s advisory are the following:
- CVE-2022-0734: Medium severity (CVSS v3.1 – 5.8) cross-site scripting vulnerability in the CGI component, allowing attackers to use a data-stealing script to snatch cookies and session tokens stored in the user’s browser.
- CVE-2022-26531: Medium severity (CVSS v3.1 – 6.1) improper validation flaw in some CLI commands, allowing a local authenticated attacker to cause a buffer overflow or system crash.
- CVE-2022-26532: High severity (CVSS v3.1 – 7.8) command injection flaw in some CLI commands, allowing a local authenticated attacker to execute arbitrary OS commands.
- CVE-2022-0910: Medium severity (CVSS v3.1 – 6.5) authentication bypass vulnerability in the CGI component, allowing an attacker to downgrade from two-factor authentication to one-factor authentication via an IPsec VPN client.
The above vulnerabilities impact USG/ZyWALL, USG FLEX, ATP, VPN, NSG firewalls, NXC2500 and NXC5500 AP controllers, and a range of Access Point products, including models of the NAP, NWA, WAC, and WAX series.
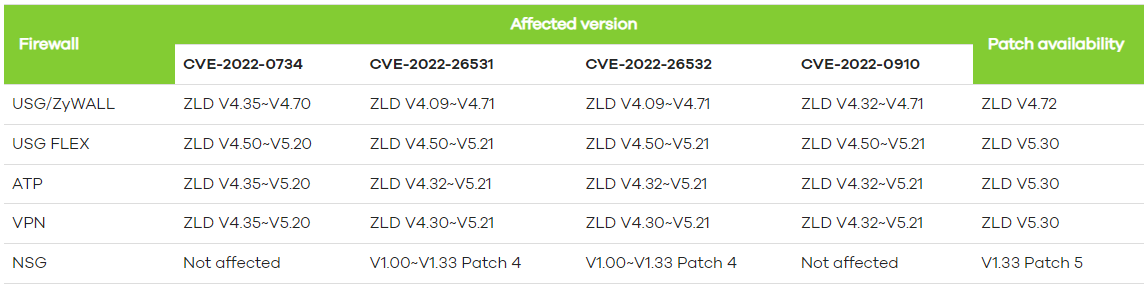
Zyxel has released the security updates that address the problems for most of the impacted models.
However, admins must request a hotfix from their local service representative for the AP controllers as a fix is not publicly available.
For the firewalls, USG/ZyWALL addresses the issues with firmware version 4.72, USG FLEX, ATP, and VPN must upgrade to ZLD version 5.30, and NSG products receive the fix via v1.33 patch 5.
While these vulnerabilities are not critical, it is still strongly advised that network admins upgrade their devices as soon as possible.
This advice is especially important for US companies as we head into a holiday weekend when it is…




