Threat Actors Use Abnormal Certificates to Deliver Info-stealing Malware
Malicious certificates can be highly dangerous as they can be used to deceive users into trusting malicious websites or software.
This can lead to various security threats, including:-
- Data breaches
- Malware infections
- Phishing attacks
- Compromise user privacy
- Compromise system integrity
Cybersecurity researchers at ASEC (AhnLab Security Emergency Response Center) recently identified that threat actors are exploiting abnormal certificates to deliver info-stealing malware.
Implementing AI-Powered Email security solutions “Trustifi” can secure your business from today’s most dangerous email threats, such as Email Tracking, Blocking, Modifying, Phishing, Account Take Over, Business Email Compromise, Malware & Ransomware
Technical Analysis
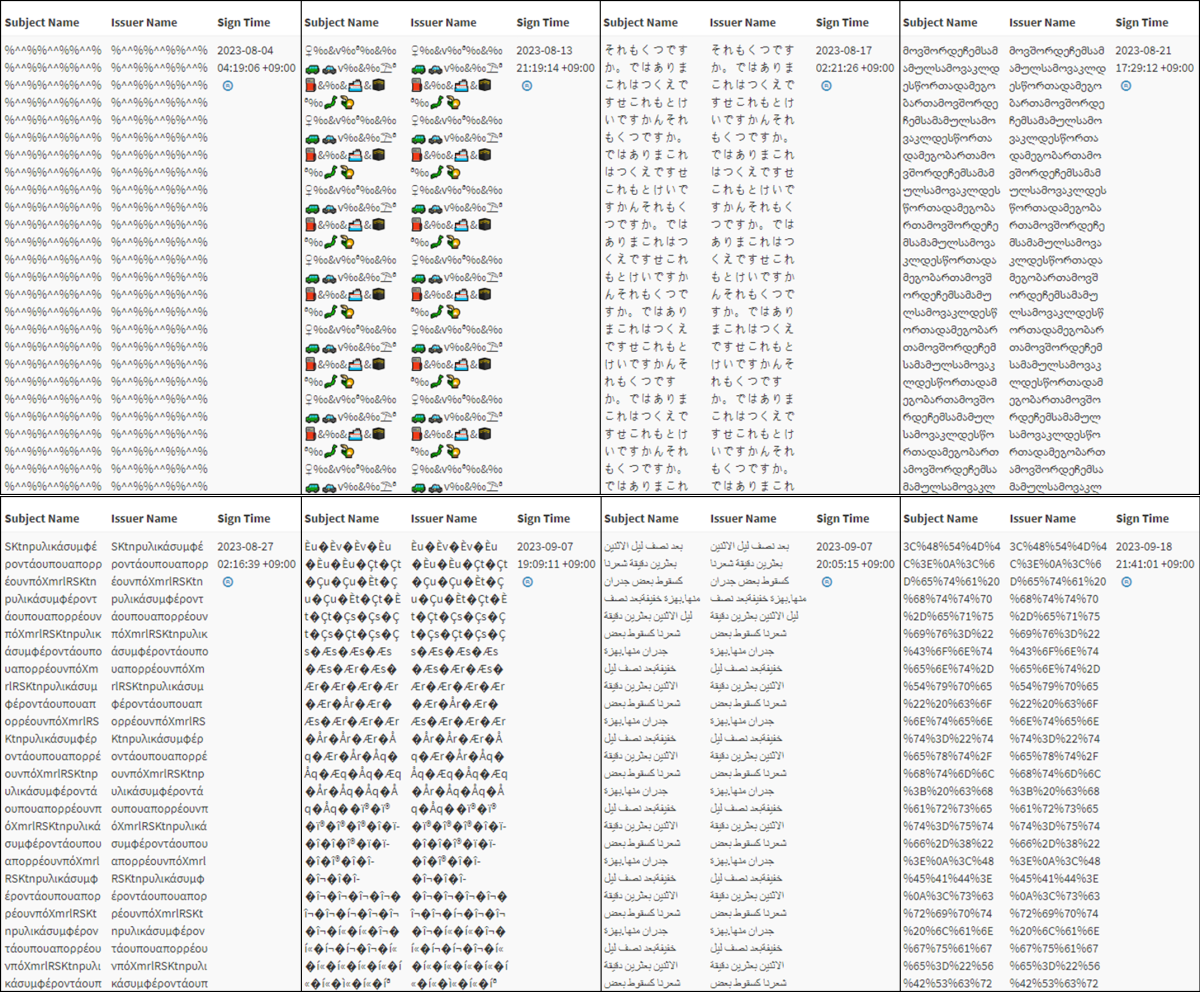
Malicious code mimics certificates with randomly entered info, causing unusually long Subject and Issuer Names.
Certificate info remains hidden in Windows, which is only detectable with specific tools. So, the incorrect certificate and its information are useless for signature verification.
The signature uses non-English languages and special characters and shows little variation for over two months, suggesting a specific intention.
The distributed sample is a URL-encoded malicious script that fails to download and execute Powershell commands, remaining inactive in the infection process.
Two distinct malware types with this distinctive appearance are distributed. And here below, we have mentioned them:
- LummaC2: LummaC2 is the most adaptable malware in this distribution. Originally, it had self-contained malicious actions, but now it downloads configs from C2 and can install other malware like Amadey and Clipbanker.
- RecordBreaker: RecoreBreaker, aka Raccoon Stealer V2, spreads through YouTube and other malware. It employs a unique User-Agent value like ‘GeekingToTheMoon’ when connecting to C2, but its functionality remains largely unchanged.
Both malware types excel in information theft, potentially exposing sensitive user data like browser…