Windows MSHTML zero-day exploits shared on hacking forums

Threat actors are sharing Windows MSHTML zero-day (CVE-2021-40444) tutorials and exploits on hacking forums, allowing other hackers to start exploiting the new vulnerability in their own attacks.
Last Tuesday, Microsoft disclosed a new zero-day vulnerability in Windows MSHTML that allows threat actors to create malicious documents, including Office and RTF docs, to execute commands on a victim’s computer remotely.
Even though there are no security updates available for the CVE-2021-40444 vulnerability, as it was discovered used in active attacks by EXPMOM and Mandiant, Microsoft decided to disclose the vulnerability and provide mitigations to help prevent its exploitation.
These mitigations work by blocking ActiveX controls and Word/RTF document previews in Windows Explorer.
However, researchers have been able to modify the exploit not to use ActiveX, effectively bypassing Microsoft’s mitigations.
Guides and PoCs shared on hacking forums
When Microsoft first disclosed the Windows MSHTML zero-day, tracked as CVE-2021-40444, security researchers quickly found the malicious documents used in attacks.
While they soon reproduced the exploits, modified them for further capabilities, and discovered a new document preview vector, the researchers did not disclose details for fear other threat actors would abuse it.
Unfortunately, threat actors have been able to reproduce the exploit on their own from information, and malicious document samples posted online and have begun sharing detailed guides and information on hacking forums.
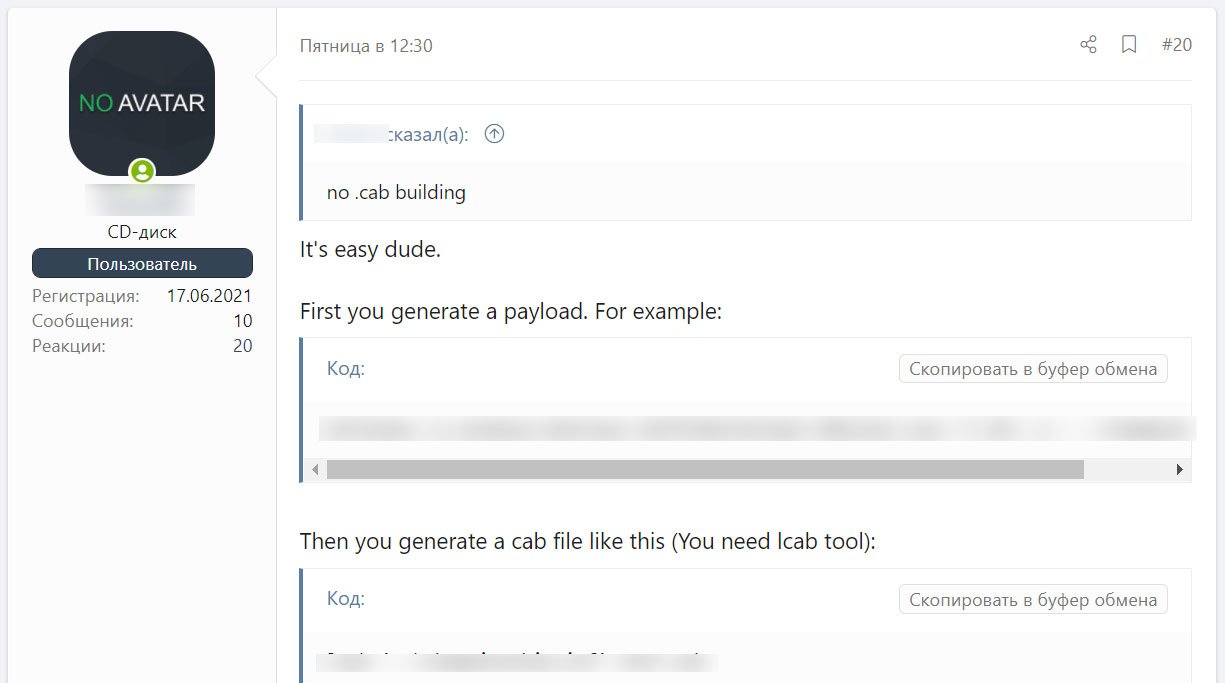
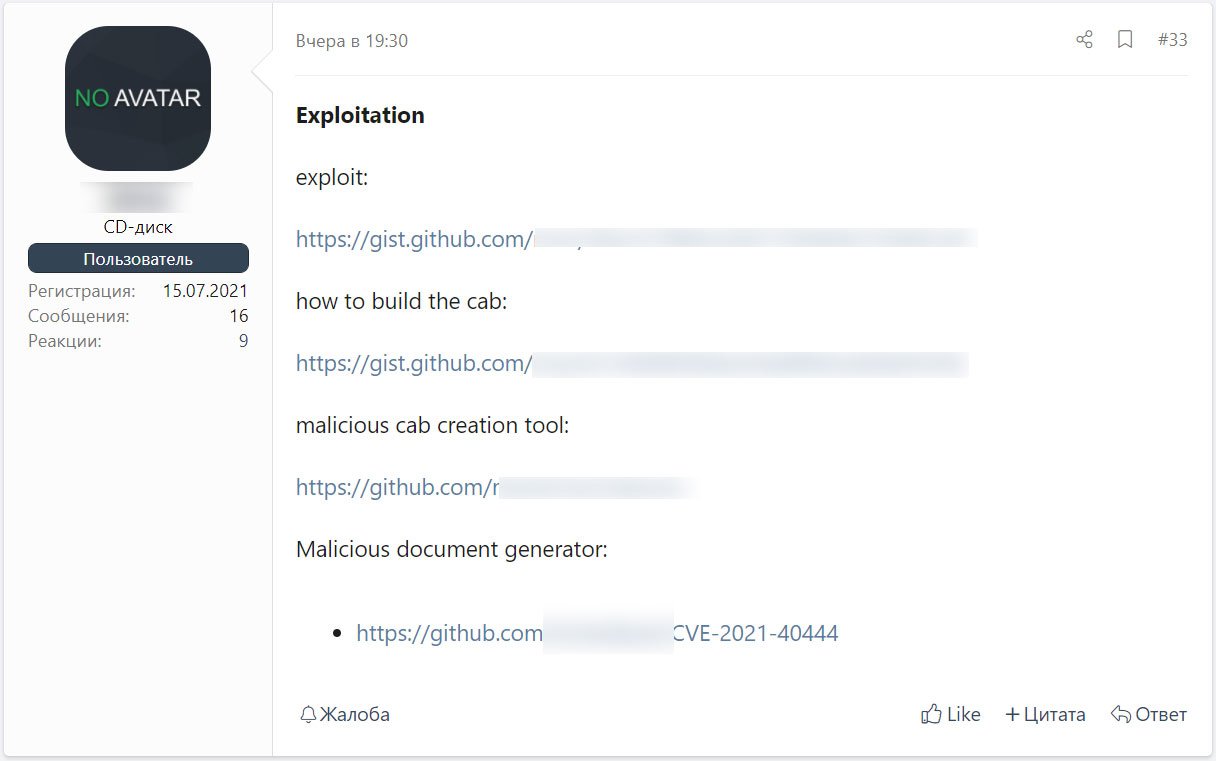
The information is simple to follow and allows anyone to create their own working version of the CVE-2021-40444 exploit, including a python server to distribute the malicious documents and CAB files.
Using this information, BleepingComputer could reproduce the exploit in about 15 minutes, as demonstrated in the video below.
Defending against the CVE-2021-40444 MSHTML vulnerability
The good news is that since the vulnerability was disclosed, Microsoft Defender and other security programs can detect and block malicious documents and CAB files used in this attack.
For example, you…


