Breaches by Iran-affiliated hackers spanned multiple U.S. states, federal agencies say
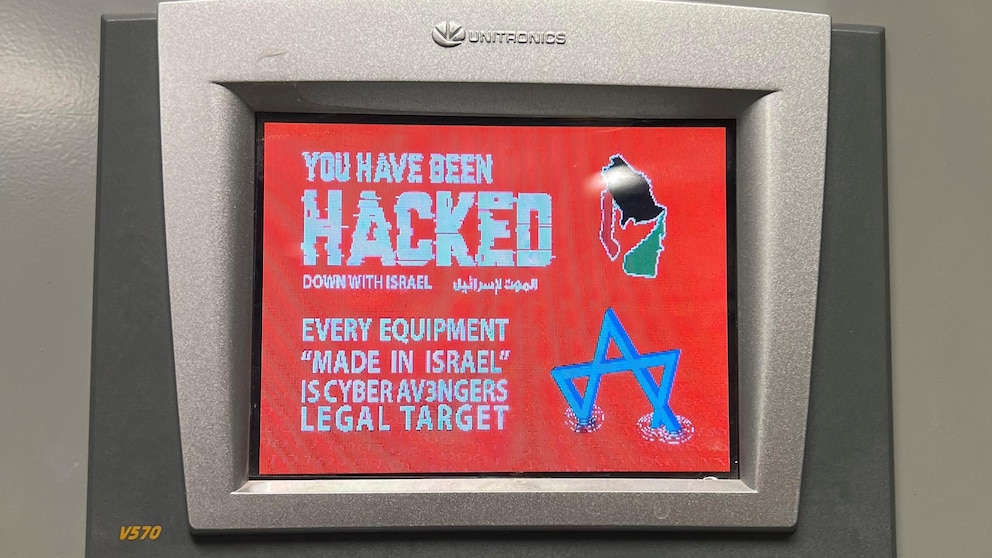
HARRISBURG, Pa. — A small western Pennsylvania water authority was just one of multiple organizations breached in the United States by Iran-affiliated hackers who targeted a specific industrial control device because it is Israeli-made, U.S. and Israeli authorities say.
“The victims span multiple U.S. states,” the FBI, the Environmental Protection Agency, the Cybersecurity and Infrastructure Security Agency, known as CISA, as well as Israel’s National Cyber Directorate said in an advisory emailed to The Associated Press late Friday.
They did not say how many organizations were hacked or otherwise describe them.
Matthew Mottes, the chairman of the Municipal Water Authority of Aliquippa, which discovered it had been hacked on Nov. 25, said Thursday that federal officials had told him the same group also breached four other utilities and an aquarium.
Cybersecurity experts say that while there is no evidence of Iranian involvement in the Oct. 7 attack into Israel by Hamas that triggered the war in Gaza they expected state-backed Iranian hackers and pro-Palestinian hacktivists to step up cyberattacks on Israeli and its allies in its aftermath. And indeed that has happened.
The multiagency advisory explained what CISA had not when it confirmed the Pennsylvania hack on Wednesday — that other industries outside water and water-treatment facilities use the same equipment — Vision Series programmable logic controllers made by Unitronics — and were also potentially vulnerable.
Those industries include “energy, food and beverage manufacturing and healthcare,” the advisory says. The devices regulate processes including pressure, temperature and fluid flow.
The Aliquippa hack promoted workers to temporarily halt pumping in a remote station that regulates water pressure for two nearby towns, leading crews to switch to manual operation. The hackers left a digital calling card on the compromised device saying all Israeli-made equipment is “a legal target.”
The multiagency advisory said it was not known if the hackers had tried to penetrate deeper into breached networks. The access they did get enabled “more profound cyber physical effects on processes and equipment,” it said.
Source…
Public security agencies wage war against hackers

Chinese police have pledged to continue to intensify their efforts on cybersecurity, as hacking into computer systems has become a major engine for criminal activities.
Statistics released by the Ministry of Public Security on Thursday showed that cybercrime has risen over the past three years at an annual average rate of 27.7 percent.
Since the start of last year, police officers across the country have solved 2,430 criminal cases involving hackers, with the capture of more than 7,000 suspects.
Highlighting the need for improving cybersecurity, Shi You, an official from the ministry, said it has stepped up efforts targeting hacking.
“While directly infiltrating and sabotaging computer information systems, criminals have also been discovered to have provided technical support and material information for other illegal activities such as telecom fraud, online gambling and online pornography,” he said.
The secondary crimes caused by hacking not only disrupt social stability and bring economic losses for people, but they also disturb market order and harm state security, he added.
In one case, for example, Beijing police detained 16 suspects involved in the fraudulent purchase and resale of tickets to scenic tourist spots in August after receiving reports from the public complaining of difficulties in booking the tickets.
The suspects were found to have illegally used software to purchase the tickets and then resell them at a higher price, the ministry said, adding that the illicit gains of the gangs were more than 2.3 million yuan ($315,000).
The capital”s police also seized 25 mobile phones, 21 computers and 26 software programs used to illegally access the tickets when they arrested the suspects, it said.
In another case, police officers in Foshan, Guangdong province, uncovered a group of 31 people in February who had allegedly obtained profits by tampering with an app’s system data.
Shi, from the ministry, stressed the focus on technology, “as the methods used by hackers have diversified with the rapid development of technologies, including artificial intelligence and blockchain”.
He expressed his concern about the…
‘Infamous Chisel’ malware threat flagged by global security agencies
A coalition of security agencies from Canada, Australia, New Zealand, the United States, and the United Kingdom has raised alarm over a new malware targeting digital currency exchanges and their wallets.
Per a joint security report, the malware targets only Android devices, stealing a trove of personal information from victims. Dubbed the “Infamous Chisel,” the malware has links with Sandworm, a state-backed entity under Russia’s military, according to the report.
The malware was originally designed to extract information from the Ukrainian military as part of a cyberwarfare strategy. However, an analysis of the inner workings of the malware indicates that its application is not limited to military use cases but extends to digital assets as well.
Infamous Chisel has been shown to extract data within the directories of digital currency exchanges, including Binance and Coinbase (NASDAQ: COIN). Per the report, the malware also extracts information from Trust Wallet, but the extent of the financial damage remains unclear.
“The malware periodically scans the device for information and files of interest, matching a predefined set of file extensions,” read the joint report. “It also contains functionality to periodically scan the local network collating information about active hosts, open ports, and banners.”
According to the report, bad actors behind the malware rely on the Tor network to cover their tracks while siphoning data from affected devices.
Despite anonymous communication tools, the joint report surmised that Infamous Chisel makes only an insignificant attempt towards the “concealment of malicious activity.” Experts say the absence of stealth techniques is linked to the lack of “host-based detection systems” for Android devices.
However, the malware makes up for its lack of stealth techniques and extensive functionalities. Aside from data extraction, Infamous Chisel is capable of traffic collection, network scanning, SSH access, remote access, SCP file transfer, and network monitoring.
Agencies contributing to the report include:
- The U.K. National Cyber Security Centre (NSCS).
- The U.S. Federal Bureau of Investigation (FBI).
- The U.S. Cybersecurity and…
FBI, European agencies announce major takedown of hacker network that used Qakbot software
LOS ANGELES — The FBI and its European partners infiltrated and seized control of a major global malware network used for more than 15 years to commit a gamut of online crimes including crippling ransomware attacks, U.S. officials said Tuesday.
They then remotely removed the malicious software agent – known as Qakbot – from thousands of infected computers.
Cybersecurity experts said they were impressed by the deft dismantling of the network but cautioned that any setback to cybercrime would likely be temporary.
“Nearly ever sector of the economy has been victimized by Qakbot,” Martin Estrada, the U.S. attorney in Los Angeles, said Tuesday in announcing the takedown.
He said the criminal network had facilitated about 40 ransomware attacks alone over 18 months that investigators said netted Qakbot administrators about $58 million.
Qakbot’s ransomware victims included an Illinois-based engineering firm, financial services organizations in Alabama and Kansas, along with a Maryland defense manufacturer and a Southern California food distribution company, Estrada said.
Officials said $8.6 million in cybercurrency was seized or frozen but no arrests were announced.
Estrada said the investigation is ongoing. He would not say where administrators of the malware, which marshaled infected machines into a botnet of zombie computers, were located. Cybersecurity researchers say they are believed to be in Russia and/or other former Soviet states.
Officials estimated the so-called malware loader, a digital Swiss knife for cybercrooks also known as Pinkslipbot and Qbot, was leveraged to cause hundreds of millions of dollars in damage since first appearing in 2008 as an information-stealing bank trojan. They said millions of people in nearly every country in the world have been affected.
Typically delivered via phishing email infections, Qakbot gave criminal hackers initial access to violated computers. They could then deploy additional payloads including ransomware, steal sensitive information or gather intelligence on victims to facilitate financial fraud and crimes such as tech support and romance scams.
The Qakbot network was “literally feeding the global cybercrime supply chain,” said Donald Alway,…