Do not download fake Anti Scam Centre app onto Android devices: Police
SINGAPORE – Those who are using Android devices are advised by the police not to download any application via an SMS that claims to be from the police’s Anti Scam Centre (ASC).
This is because the Android package kit (APK) file may contain malware which allows scammers to access and take control of the device remotely, and to steal passwords in the device, the police said on Sunday.
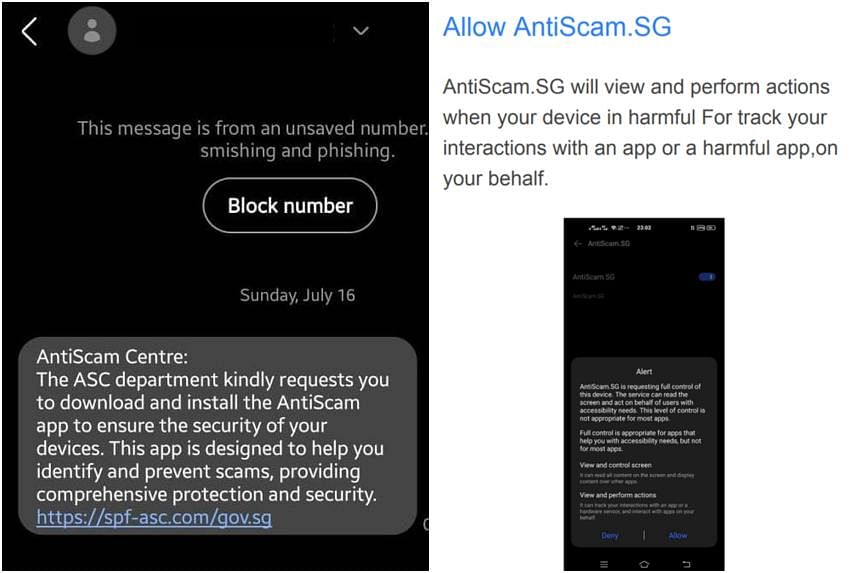
In this scam variant, members of the public are sent an SMS claiming to be from ASC and requesting them to download and install an anti-scam app to ensure the security of their devices.
According to the police, the fake app claims to help identify and prevent scams by providing comprehensive protection and security.
The SMS contains a URL link to a fake ASC website with a link to download the app. As part of the app installation, the Android user would be prompted to allow access to the device to enable the anti-scam service.
Those with information relating to such crimes, or who are in doubt, can call the police hotline on 1800-255-0000, or submit it online at www.police.gov.sg/iwitness.