Troy Hunt at Black Hat Asia: ‘We’re making it very difficult for people to make good security decisions’
Have I Been Pwned founder’s keynote offered a sobering counterpoint to the well-meaning ‘World Password Day’

Imagine a parent’s terror when the geolocation of their child’s smart watch suddenly switches from tennis practice to the middle of the ocean.
This was precisely the scenario simulated by Ken Munro of UK infosec firm Pen Test Partners via exploitation of an insecure direct object reference (IDOR) vulnerability in an IoT device, and with help from Troy Hunt, creator of data breach record index Have I Been Pwned, and his daughter.
This was one of many eye-opening tales of shoddy security behind the “endless flow of data” into Have I Been Pwned recounted today (May 6) during Hunt’s keynote address at the all-virtual Black Hat Asia 2021.
Another API flaw in the TicTocTrack kids watch meant Munro’s colleague, Vangelis Stykas, successfully initiated a voice call through the device with zero interaction required from the wearer.
Logged into his own account, Munro also compromised other ‘family’ accounts by simply changing an identifier parameter. A subsequent security patch created an even more egregious regression bug.
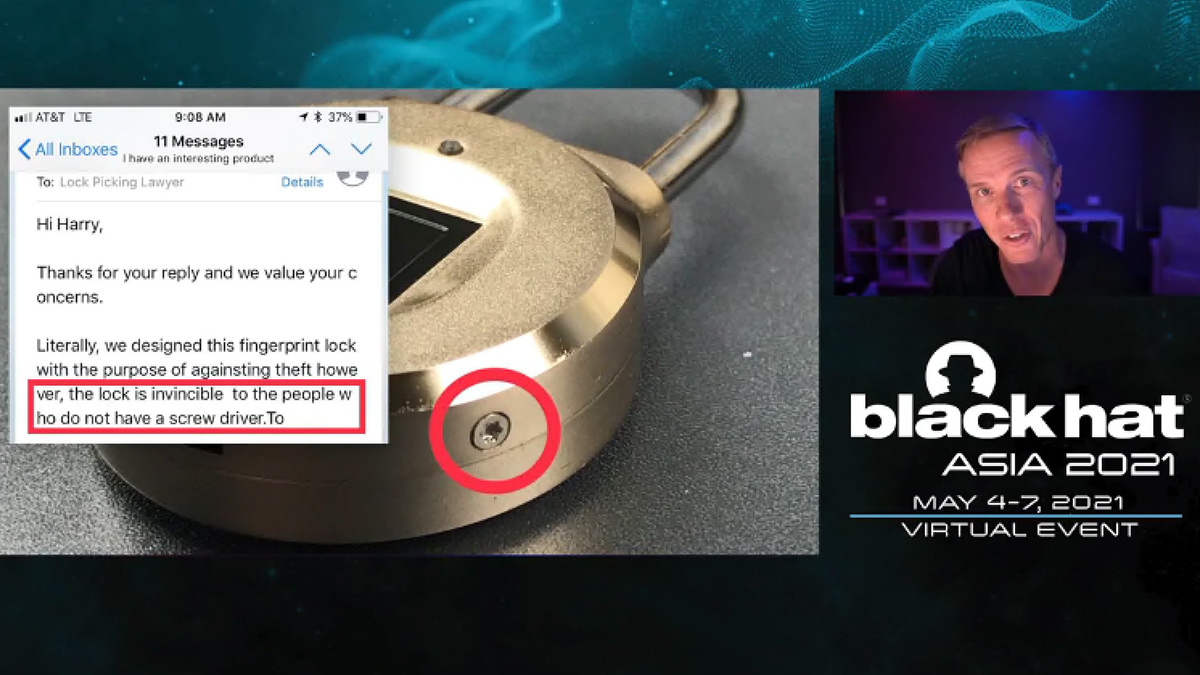
Hunt also cited a purely physical intrusion that nevertheless “perfectly illustrates” his digital insecurity theme.
Having notified the vendor that he had dismantled their $47.99 biometric lock, a popular YouTube lock-picker was told the contraption was “invincible to people who do not have a screwdriver”.
Phishy email marketing
During his keynote, Hunt noted that even supposedly security-conscious organizations are “making it very difficult for people to make good security decisions”.
The infosec pro cited a ‘phishy’ email he received from Australia’s ANZ Bank featuring a suspicious, HTTP URL that redirected to another suspicious URL: ‘c00.adobe.com’.
The email turned out to be a genuine ANZ communication.
“Over and over again”, lamented Hunt, we see “legitimate organizations sending legitimate communications that are indistinguishable from phishing attacks”.
 Australian infosec pro Troy Hunt delivered the Black Hat Asia 2021 keynote
Australian infosec pro Troy Hunt delivered the Black Hat Asia 2021 keynote
Publicly accessible databases
Founded in 2013, Have…