Ways to Implement Multifactor Authentication Without a Mobile Device
Passwords are hard to remember and even harder to change periodically, and it’s increasingly difficult to devise strong credentials. Instead of confronting the challenge, many users rely on weak passwords and reuse them for multiple accounts. This makes it easy for cybercriminals to guess credentials or obtain them via phishing attacks.
Once gathered, credentials can be sold on the dark web. Then, both the original criminal and hordes of other attackers can gain access to personal and work-related systems and data.
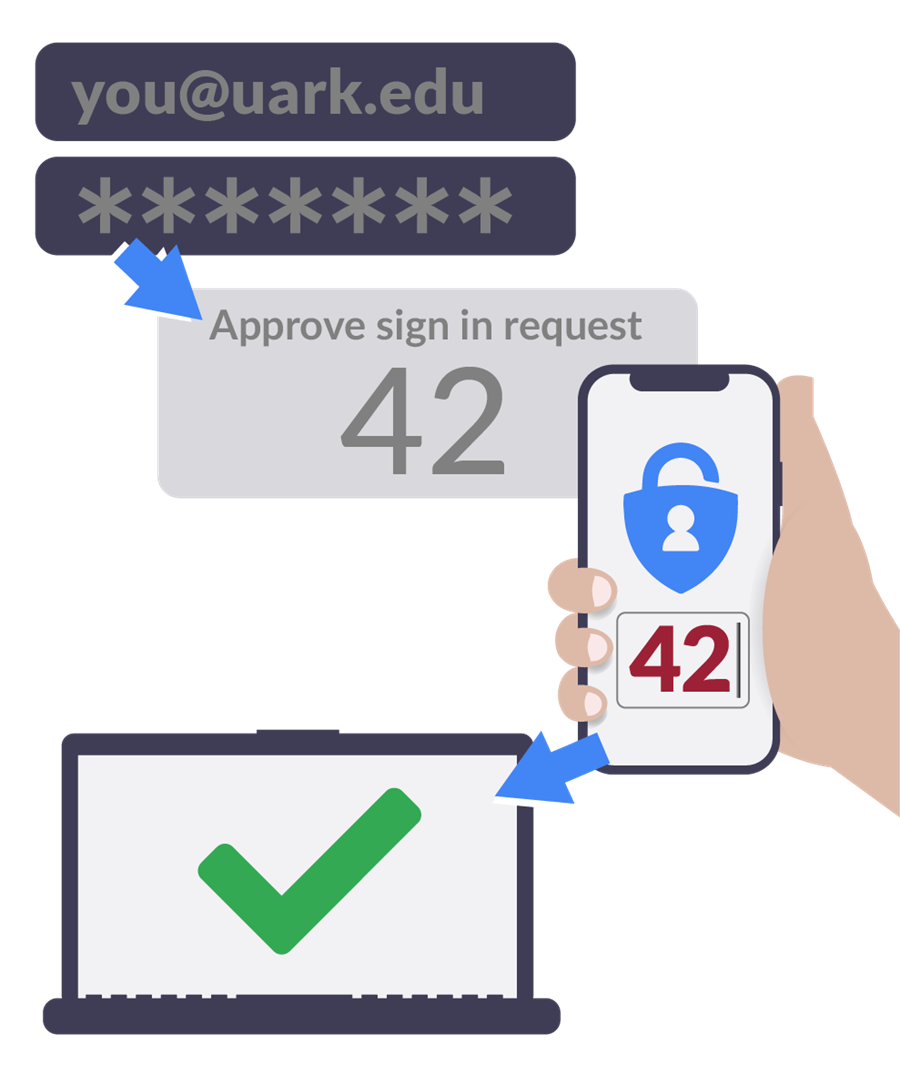
Two-factor authentication (2FA) and multifactor authentication (MFA) are accepted ways to make credentials much less vulnerable. 2FA relies on a combination of something you know (e.g., username/password) and something you have (e.g., your mobile phone or computer, a keycard or a USB) or something you are (e.g., a scan of your iris or fingerprint) to ensure that only authorized individuals can access sensitive systems and information.
MFA can involve all three factors. With MFA, even if the username/password combination is stolen, accessing an account is extremely difficult because criminals won’t be able to complete the additional authentication steps.
Click the banner to access customized content when you register as an Insider.
When MFA and Mobile Devices Don’t Mix
Common methods of implementing MFA often rely on the use of mobile devices. When an SMS message, a one-time password or a push notification is sent, it is commonly delivered to a user’s smartphone. That said, there are some risks associated with sending SMS, one-time password or push notifications for MFA. When implemented improperly or as the sole security method, messages could be hacked and codes intercepted. In fact, the U.S. government has recommended that no MFA solution should rely solely on SMS verification tools.
Ensuring Protection Outside of Mobile-Based MFA
To fill these gaps and ensure 100 percent MFA coverage, agencies may consider hardware security keys. The key is typically a physical device, often a USB drive that only grants access to accounts while it is plugged into a computer. It provides a high level of protection against phishing and hacking because no…