Is Samsung Pay safe? – Android Authority
Samsung Pay is a mobile payment app available exclusively on Samsung smartphones and smartwatches, making it easy to make quick purchases on the go. It’s convenient and lets you leave your wallet behind. But many users might be wary about saving their card information on a device that others might access or could be lost or stolen. So, is Samsung Pay safe?
Read more: How to set up and use Samsung Pay
QUICK ANSWER
Yes, Samsung Pay is safe. The app doesn’t store your actual card information and uses tokenization to create a unique identifier used to complete transactions. You also cannot make a purchase without first authenticating it with a PIN, pattern, fingerprint, or face scan. Samsung phones also come with Knox to protect your phone from malware and other security threats.
JUMP TO KEY SECTIONS
How secure is Samsung Pay?

Edgar Cervantes / Android Authority
Samsung provides as much security as possible with Samsung Pay to ensure that your private financial information is safe. Knox, Samsung’s multi-layer software protection system, protects your phone from malware and other security threats and keeps personal info like passwords, card information, biometrics, and more secure.
The Samsung Pay app uses tokenization to secure your card data. In simple terms, tokenization replaces your card info with another unique identifier that is then used to complete the transaction on the payment network. When you add a card to Samsung Pay, you will see a different number under your card called the Digital card number. If anyone requires the last four digits of your card to verify a transaction, this is the number you’ll provide instead of your actual card details.
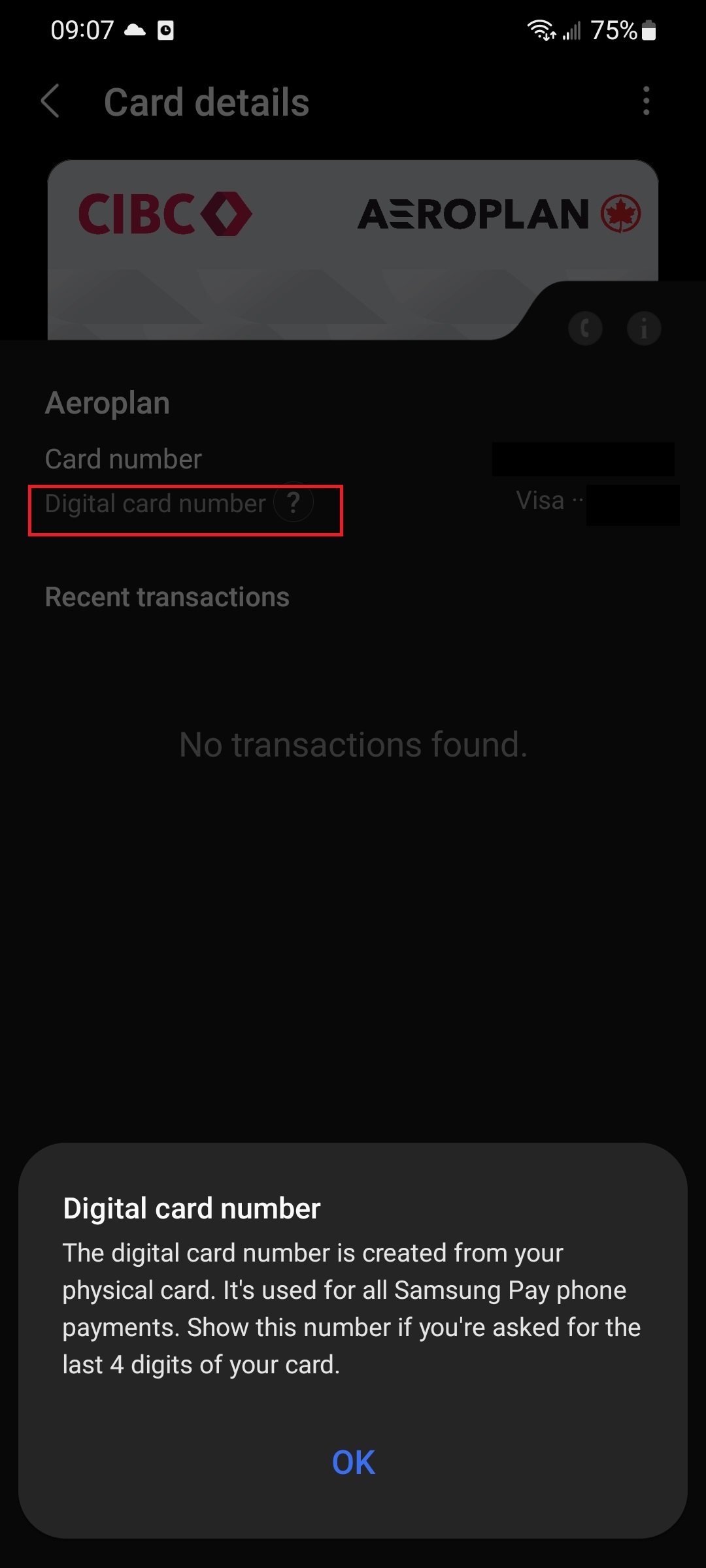
Ankit Banerjee / Android Authority
Your actual card information isn’t saved or accessed by Samsung, with the app using the created token for transactions. Samsung Pay will only show the last four digits of your card number on the image to make it easier to find and manage if you add multiple cards.
Samsung ensures that every step when using Samsung Pay is safe as well. You will need to authorize every transaction with a PIN, pattern, fingerprint, or iris scan before completing a purchase. When you add a card, the bank or card…




