Hackers abusing OAuth to automate cyber attacks, says Microsoft
Threat actors are misusing OAuth-based applications as an automation tool for authentication, says Microsoft.
“Threat actors compromise user accounts to create, modify, and grant high privileges to OAuth applications that they can misuse to hide malicious activity,” the company said in a blog this week. “The misuse of OAuth also enables threat actors to maintain access to applications even if they lose access to the initially compromised account.”
Threat actors are launching phishing or password-spraying attacks to compromise user accounts that don’t have strong authentication mechanisms and have permissions to create or modify OAuth applications. The attackers misuse the OAuth applications with high privilege permissions to deploy virtual machines (VMs) for cryptocurrency mining, establish persistence following business email compromise (BEC), and launch spamming activity using the targeted organization’s resources and domain name.
IT managers should take the following steps to mitigate against OAuth abuse:
— implement security practices that strengthen account credentials, such as enabling multifactor authentication. That dramatically reduces the chance of attack, says Microsoft;
— to protect against attacks that leverage stolen credentials, enable conditional risk-based access policies;
— ensure continuous access evaluation is enabled if available in your environment;
— enable all security defaults in identity platforms;
— audit all apps and consented permissions to ensure applications are only accessing necessary data and adhering to the principles of least privilege access.
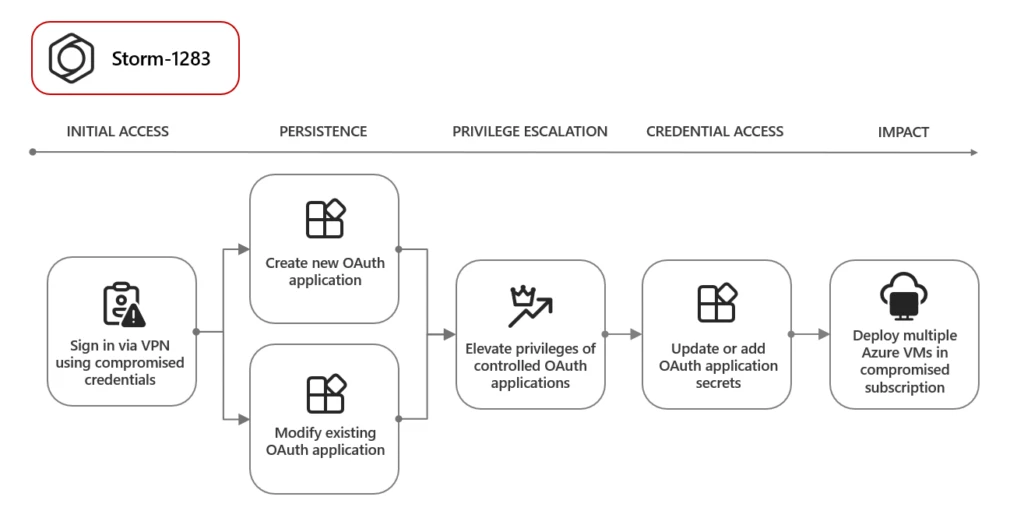
The report gives an example of what one threat actor, which Microsoft dubs Storm-1283, is doing. (Under Microsoft’s new naming taxonomy, groups dubbed ‘Storm’ are newly discovered or under development.)
Storm-1283 used a compromised user account to create an OAuth application and deploy VMs for cryptomining. The compromised account allowed the attacker to sign in through a VPN, create a new single-tenant OAuth application in Microsoft Entra ID named similarly to the Microsoft Entra ID tenant domain name, and add a set of secrets to the application.